Ethical Hacking 简明教程
Ethical Hacking - Overview
黑客活动已经成为计算机当中的一部分,已经有将近 50 年的历史,而且它是一个非常广泛的学科,涵盖了广泛的主题。第一次已知的黑客事件发生在 1960 年的麻省理工学院,同时,“黑客”这个术语也随之产生。
Hacking has been a part of computing for almost five decades and it is a very broad discipline, which covers a wide range of topics. The first known event of hacking had taken place in 1960 at MIT and at the same time, the term "Hacker" was originated.
黑客行为是查找计算机系统或计算机网络中存在的可能的入侵点,然后最终进入到该系统或网络的行为。黑客行为通常是为了获得对计算机系统或计算机网络的未经授权的访问,以便损害系统或窃取计算机上可用的敏感信息。
Hacking is the act of finding the possible entry points that exist in a computer system or a computer network and finally entering into them. Hacking is usually done to gain unauthorized access to a computer system or a computer network, either to harm the systems or to steal sensitive information available on the computer.
只要黑客行为是为了在计算机或网络系统中发现弱点以便进行测试,那么这种黑客行为通常是合法的。这种类型的黑客行为就是我们所称的 Ethical Hacking 。
Hacking is usually legal as long as it is being done to find weaknesses in a computer or network system for testing purpose. This sort of hacking is what we call Ethical Hacking.
A computer expert who does the act of hacking is called a "Hacker". Hackers are those who seek knowledge, to understand how systems operate, how they are designed, and then attempt to play with these systems.
Types of Hacking
We can segregate hacking into different categories, based on what is being hacked. Here is a set of examples −
-
Website Hacking − Hacking a website means taking unauthorized control over a web server and its associated software such as databases and other interfaces.
-
Network Hacking − Hacking a network means gathering information about a network by using tools like Telnet, NS lookup, Ping, Tracert, Netstat, etc. with the intent to harm the network system and hamper its operation.
-
Email Hacking − It includes getting unauthorized access on an Email account and using it without taking the consent of its owner.
-
Ethical Hacking − Ethical hacking involves finding weaknesses in a computer or network system for testing purpose and finally getting them fixed.
-
Password Hacking − This is the process of recovering secret passwords from data that has been stored in or transmitted by a computer system.
-
Computer Hacking − This is the process of stealing computer ID and password by applying hacking methods and getting unauthorized access to a computer system.
Advantages of Hacking
黑客在以下情况下非常有用——
Hacking is quite useful in the following scenarios −
-
To recover lost information, especially in case you lost your password.
-
To perform penetration testing to strengthen computer and network security.
-
To put adequate preventative measures in place to prevent security breaches.
-
To have a computer system that prevents malicious hackers from gaining access.
Disadvantages of Hacking
如果黑客行为出于恶意,则非常危险。它会导致——
Hacking is quite dangerous if it is done with harmful intent. It can cause −
-
Massive security breach.
-
Unauthorized system access on private information.
-
Privacy violation.
-
Hampering system operation.
-
Denial of service attacks.
-
Malicious attack on the system.
Purpose of Hacking
There could be various positive and negative intentions behind performing hacking activities. Here is a list of some probable reasons why people indulge in hacking activities −
-
Just for fun
-
Show-off
-
Steal important information
-
Damaging the system
-
Hampering privacy
-
Money extortion
-
System security testing
-
To break policy compliance
Ethical Hacking - Hacker Types
根据他们入侵系统的意图,黑客可分类为不同的类别,例如白帽子、黑帽子和灰帽子。这些不同的术语来自老式西部片,其中坏蛋戴黑色牛仔帽,好人戴白帽子。
Hackers can be classified into different categories such as white hat, black hat, and grey hat, based on their intent of hacking a system. These different terms come from old Spaghetti Westerns, where the bad guy wears a black cowboy hat and the good guy wears a white hat.
White Hat Hackers
白帽黑客又称 Ethical Hackers 。他们永远不会打算伤害一个系统,而是尝试找出计算机或网络系统中的软肋,作为渗透测试和安全漏洞评估的一部分。
White Hat hackers are also known as Ethical Hackers. They never intent to harm a system, rather they try to find out weaknesses in a computer or a network system as a part of penetration testing and vulnerability assessments.
道德黑客并不违法,并且是 IT 行业中可获得的极具挑战性的一份工作。有许多公司聘用道德黑客进行渗透测试和安全漏洞评估。
Ethical hacking is not illegal and it is one of the demanding jobs available in the IT industry. There are numerous companies that hire ethical hackers for penetration testing and vulnerability assessments.
Black Hat Hackers
黑帽黑客又称 crackers ,他们通过入侵来获取对系统的未授权访问权限,然后妨碍系统运营或窃取敏感信息。
Black Hat hackers, also known as crackers, are those who hack in order to gain unauthorized access to a system and harm its operations or steal sensitive information.
黑帽黑客总是是非法的,因为其恶意目的包括窃取公司数据、侵犯隐私、破坏系统、阻断网络通信等。
Black Hat hacking is always illegal because of its bad intent which includes stealing corporate data, violating privacy, damaging the system, blocking network communication, etc.
Grey Hat Hackers
灰帽黑客是黑帽和白帽黑客的混合体。他们会采取行动,但并非出于恶意目的。出于自己兴趣的目的,他们会在未经所有人许可或不知情的情况下利用计算机系统或网络中的安全漏洞。
Grey hat hackers are a blend of both black hat and white hat hackers. They act without malicious intent but for their fun, they exploit a security weakness in a computer system or network without the owner’s permission or knowledge.
他们的目的是引起所有人的注意,并从所有人那里得到赞赏或少量奖励金。
Their intent is to bring the weakness to the attention of the owners and getting appreciation or a little bounty from the owners.
Miscellaneous Hackers
除了上述众所周知的黑客类别外,我们还有基于他们所入侵的内容及方式对其进行划分的以下黑客类别:
Apart from the above well-known classes of hackers, we have the following categories of hackers based on what they hack and how they do it −
Red Hat Hackers
红帽黑客再次是黑帽和白帽黑客的混合体。通常他们的层次是入侵政府机构、最高机密的信息中心,以及一般归属于敏感信息类别中的一切。
Red hat hackers are again a blend of both black hat and white hat hackers. They are usually on the level of hacking government agencies, top-secret information hubs, and generally anything that falls under the category of sensitive information.
Blue Hat Hackers
蓝帽黑客是指在计算机安全咨询公司之外受雇于系统发布前进行故障测试的人员。他们寻找可以利用的漏洞,并尝试关闭这些漏洞。微软也使用术语 BlueHat 来代表一系列安全简报事件。
A blue hat hacker is someone outside computer security consulting firms who is used to bug-test a system prior to its launch. They look for loopholes that can be exploited and try to close these gaps. Microsoft also uses the term BlueHat to represent a series of security briefing events.
Elite Hackers
这是黑客中的一种社交地位,用于表明技术最娴熟的人员。新发现的漏洞会在这些黑客之间流传。
This is a social status among hackers, which is used to describe the most skilled. Newly discovered exploits will circulate among these hackers.
Script Kiddie
脚本小子是一个非专家,他们使用别人编写的事先封装的自动化工具入侵计算机系统,通常对底层概念了解甚少,因此有了 Kiddie 一词。
A script kiddie is a non-expert who breaks into computer systems by using pre-packaged automated tools written by others, usually with little understanding of the underlying concept, hence the term Kiddie.
Ethical Hacking - Famous Hackers
在本章中,我们将简要了解一些著名的黑客以及他们如何成名的内容。
In this chapter, we will have a brief synopsis of some of the famous Hackers and how they became famous.
Jonathan James

乔纳森·詹姆斯是一位美国黑客,因成为美国历史上第一个因网络犯罪被判入狱的未成年人而臭名昭著。2008 年,他因自伤枪伤而自杀。
Jonathan James was an American hacker, illfamous as the first juvenile sent to prison for cybercrime in United States. He committed suicide in 2008 of a self-inflicted gunshot wound.
1999 年,年仅 16 岁的他就通过破解属于美国宇航局的服务器的密码来访问多台计算机,窃取了国际空间站的源代码以及其他敏感信息。
In 1999, at the age of 16, he gained access to several computers by breaking the password of a server that belonged to NASA and stole the source code of the International Space Station among other sensitive information.
Ian Murphy

伊恩·墨菲,也称为 Captain Zap,曾一度让高中生为他盗取计算机设备。伊恩自称是“第一个因犯罪而被定罪的黑客”。
Ian Murphy, also known as Captain Zap, at one point of time was having high school students steal computer equipment for him. Ian selfproclaims to have been "the first hacker ever convicted of a crime".
1986 年,伊恩与其失业的妻子决定组建某种类型的企业后,他作为顶级黑客的职业生涯就被捏造了。
Ian’s career as a master hacker was fabricated in 1986 after he and his unemployed wife decided to form some type of business.
他有着悠久的计算机和互联网诈骗历史。他的一个最喜欢的游戏是伪造电子邮件头信息并发送第三方威胁信。
He has a long history of computer and Internet frauds. One of his favourite games is to forge Email headers and to send out third-party threat letters.
Kevin Mitnick

凯文·米特尼克是一位计算机安全顾问兼作者,他潜入其客户的公司来揭示他们的安全优势、劣势和潜在漏洞。
Kevin Mitnick is a computer security consultant and author, who infiltrates his clients’ companies to expose their security strengths, weaknesses, and potential loopholes.
他是第一个将他的脸永生在联邦调查局“最想通缉”海报上的黑客。他曾是美国历史上最受通缉的计算机罪犯。
He is the first hacker to have his face immortalized on an FBI "Most Wanted" poster. He was formerly the most wanted computer criminal in the history of United States.
从 20 世纪 70 年代直到 1995 年被最后一次逮捕,他熟练地绕过了公司安全保障,并且进入了一些戒备最森严的系统,例如 Sun Microsystems、Digital Equipment Corporation、Motorola、Netcom 和 Nokia。
From the 1970s up until his last arrest in 1995, he skilfully bypassed corporate security safeguards, and found his way into some of the most well-guarded systems such as Sun Microsystems, Digital Equipment Corporation, Motorola, Netcom, and Nokia.
Mark Abene

马克·阿贝以其化名 Phiber Optik 闻名于世,是一位信息安全专家兼企业家。他在 20 世纪 80 年代和 90 年代初期是一位备受瞩目的黑客。他是最早公开争论并捍卫道德黑客作为对行业有益的工具的积极优点的黑客之一。
Mark Abene, known around the world by his pseudonym Phiber Optik, is an information security expert and entrepreneur. He was a high-profile hacker in the 1980s and early 1990s. He was one of the first hackers to openly debate and defend the positive merits of ethical hacking as a beneficial tool to industry.
他的专业知识领域包括渗透研究、现场安全评估、安全代码审查、安全策略审查和生成、系统和网络架构、系统管理和网络管理等诸多方面。他的客户包括美国运通、瑞银集团、富国银行、安永、毕马威等。
His expertise spreads across penetration studies, on-site security assessments, secure code reviews, security policy review and generation, systems and network architecture, systems administration and network management, among many others. His clientele includes American Express, UBS, First USA, Ernst & Young, KPMG and others.
Johan Helsinguis

尤汉·赫尔辛吉厄斯,更为人所知的名字是 Julf,他于 20 世纪 80 年代进入公众视野,当时他开始运营世界上最受欢迎的匿名 remailer penet.fi。
Johan Helsingius, better known as Julf, came into the limelight in the 1980s when he started operating the world’s most popular anonymous remailer, called penet.fi.
尤汉还负责第一个泛欧互联网服务提供商 Eunet International 的产品开发。
Johan was also responsible for product development for the first Pan-European internet service provider, Eunet International.
目前,他是阿姆斯特丹黑客空间协会 Technologia Incognita 的董事会成员,并用他的网络知识为全球通信公司提供支持。
He is at present, a member of the board of Technologia Incognita, a hackerspace association in Amsterdam, and supports the communication companies worldwide with his cyber knowledge.
Linus Torvalds

林纳斯·托瓦兹被认为是有史以来最优秀的黑客之一。他通过创建广受欢迎的类 Unix 操作系统 Linux 而声名鹊起。Linux 是开源的,成千上万的开发人员都为其内核做出了贡献。但是,托瓦兹仍然是决定哪些新代码并入 Linux 标准内核的最终权威。截至 2006 年,大约有 2% 的 Linux 内核是由托瓦兹本人编写的。
Linus Torvalds is known as one of the best hackers of all time. He rose to fame by creating Linux, the very popular Unix-based operating system. Linux is open source and thousands of developers have contributed to its Kernel. However, Torvalds remains the ultimate authority on what new code is incorporated into the standard Linux kernel. As of 2006, approximately two percent of the Linux kernel was written by Torvalds himself.
他只是渴望简单的生活和开发出世界上最好的操作系统来获得乐趣。托瓦兹获得过斯德哥尔摩大学和赫尔辛基大学的荣誉博士学位。
He just aspires to be simple and have fun by making the world’s best operating system. Torvalds has received honorary doctorates from Stockholm University and University of Helsinki.
Robert Morris

罗伯特·莫里斯,即 Morris 蠕虫的创建者,Morris 蠕虫是第一个在互联网上释放的蠕虫。该蠕虫具有使计算机速度变慢并使其无法继续使用的能力。因此,他被判处缓刑三年、400 小时的社区服务并且还必须支付 10500 美元的罚款。
Robert Morris, known as the creator of the Morris Worm, the first computer worm to be unleashed on the Internet. The worm had the capability to slow down computers and make them no longer usable. As a result of this, he was sentenced to three years’ probation, 400 hours of community service and also had to pay a penalty amount of $10,500.
莫里斯目前在麻省理工学院计算机科学与人工智能实验室担任终身教授。
Morris is currently working as a tenured professor at the MIT Computer Science and Artificial Intelligence Laboratory.
Gary McKinnon

加里·麦金农是一位著名的系统管理员和黑客。他因被指控“史上最大的针对军事计算机的黑客攻击”而闻名。他已经成功入侵了美国政府的陆军、空军、海军和 NASA 系统的网络。
Gary McKinnon is a renowned systems administrator and hacker. He was famously accused of the “biggest military computer hack of all time”. He had successfully hacked the networks of Army, Air Force, Navy and NASA systems of the United States government.
在他的媒体声明中,他经常提到他的动机只是找到 UFO、反重力技术以及可能会对公众有用的“免费能源”被压制掉的证据。
In his statements to the media, he has often mentioned that his motivation was only to find evidence of UFOs, antigravity technology, and the suppression of “free energy” that could potentially be useful to the public.
Kevin Poulsen

凯文·鲍尔森,又名 Dark Dante ,因接管洛杉矶电台 KIIS-FM 的所有电话线路而声名鹊起,并保证他将成为第 102 位来电者并赢得保时捷 944 S2 的大奖。
Kevin Poulsen, also known as Dark Dante, became famous for his notoriety when he took over all the telephone lines of Los Angeles radio station KIIS-FM, guaranteeing that he would be the 102nd caller and win the prize of a Porsche 944 S2.
当鲍尔森黑进联邦计算机以获取窃听信息时,他也引起了联邦调查局的愤怒,因此他不得不服刑五年。他重新塑造了自己成为一名记者,在这个领域为自己开辟了一个利基市场。
Poulsen also drew the ire of FBI, when he hacked into federal computers for wiretap information, for which he had to serve a sentence of five years. He has reinvented himself as a journalist and has carved a niche for himself in this field.
Ethical Hacking - Terminologies
以下是黑客领域中使用的一些重要术语。
Following is a list of important terms used in the field of hacking.
-
Adware − Adware is software designed to force pre-chosen ads to display on your system.
-
Attack − An attack is an action that is done on a system to get its access and extract sensitive data.
-
Back door − A back door, or trap door, is a hidden entry to a computing device or software that bypasses security measures, such as logins and password protections.
-
Bot − A bot is a program that automates an action so that it can be done repeatedly at a much higher rate for a more sustained period than a human operator could do it. For example, sending HTTP, FTP or Telnet at a higher rate or calling script to create objects at a higher rate.
-
Botnet − A botnet, also known as zombie army, is a group of computers controlled without their owners’ knowledge. Botnets are used to send spam or make denial of service attacks.
-
Brute force attack − A brute force attack is an automated and the simplest kind of method to gain access to a system or website. It tries different combination of usernames and passwords, over and over again, until it gets in.
-
Buffer Overflow − Buffer Overflow is a flaw that occurs when more data is written to a block of memory, or buffer, than the buffer is allocated to hold.
-
Clone phishing − Clone phishing is the modification of an existing, legitimate email with a false link to trick the recipient into providing personal information.
-
Cracker − A cracker is one who modifies the software to access the features which are considered undesirable by the person cracking the software, especially copy protection features.
-
Denial of service attack (DoS) − A denial of service (DoS) attack is a malicious attempt to make a server or a network resource unavailable to users, usually by temporarily interrupting or suspending the services of a host connected to the Internet.
-
DDoS − Distributed denial of service attack.
-
Exploit Kit − An exploit kit is software system designed to run on web servers, with the purpose of identifying software vulnerabilities in client machines communicating with it and exploiting discovered vulnerabilities to upload and execute malicious code on the client.
-
Exploit − Exploit is a piece of software, a chunk of data, or a sequence of commands that takes advantage of a bug or vulnerability to compromise the security of a computer or network system.
-
Firewall − A firewall is a filter designed to keep unwanted intruders outside a computer system or network while allowing safe communication between systems and users on the inside of the firewall.
-
Keystroke logging − Keystroke logging is the process of tracking the keys which are pressed on a computer (and which touchscreen points are used). It is simply the map of a computer/human interface. It is used by gray and black hat hackers to record login IDs and passwords. Keyloggers are usually secreted onto a device using a Trojan delivered by a phishing email.
-
Logic bomb − A virus secreted into a system that triggers a malicious action when certain conditions are met. The most common version is the time bomb.
-
Malware − Malware is an umbrella term used to refer to a variety of forms of hostile or intrusive software, including computer viruses, worms, Trojan horses, ransomware, spyware, adware, scareware, and other malicious programs.
-
Master Program − A master program is the program a black hat hacker uses to remotely transmit commands to infected zombie drones, normally to carry out Denial of Service attacks or spam attacks.
-
Phishing − Phishing is an e-mail fraud method in which the perpetrator sends out legitimate-looking emails, in an attempt to gather personal and financial information from recipients.
-
Phreaker − Phreakers are considered the original computer hackers and they are those who break into the telephone network illegally, typically to make free longdistance phone calls or to tap phone lines.
-
Rootkit − Rootkit is a stealthy type of software, typically malicious, designed to hide the existence of certain processes or programs from normal methods of detection and enable continued privileged access to a computer.
-
Shrink Wrap code − A Shrink Wrap code attack is an act of exploiting holes in unpatched or poorly configured software.
-
Social engineering − Social engineering implies deceiving someone with the purpose of acquiring sensitive and personal information, like credit card details or user names and passwords.
-
Spam − A Spam is simply an unsolicited email, also known as junk email, sent to a large number of recipients without their consent.
-
Spoofing − Spoofing is a technique used to gain unauthorized access to computers, whereby the intruder sends messages to a computer with an IP address indicating that the message is coming from a trusted host.
-
Spyware − Spyware is software that aims to gather information about a person or organization without their knowledge and that may send such information to another entity without the consumer’s consent, or that asserts control over a computer without the consumer’s knowledge.
-
SQL Injection − SQL injection is an SQL code injection technique, used to attack data-driven applications, in which malicious SQL statements are inserted into an entry field for execution (e.g. to dump the database contents to the attacker).
-
Threat − A threat is a possible danger that can exploit an existing bug or vulnerability to compromise the security of a computer or network system.
-
Trojan − A Trojan, or Trojan Horse, is a malicious program disguised to look like a valid program, making it difficult to distinguish from programs that are supposed to be there designed with an intention to destroy files, alter information, steal passwords or other information.
-
Virus − A virus is a malicious program or a piece of code which is capable of copying itself and typically has a detrimental effect, such as corrupting the system or destroying data.
-
Vulnerability − A vulnerability is a weakness which allows a hacker to compromise the security of a computer or network system.
-
Worms − A worm is a self-replicating virus that does not alter files but resides in active memory and duplicates itself.
-
Cross-site Scripting − Cross-site scripting (XSS) is a type of computer security vulnerability typically found in web applications. XSS enables attackers to inject client-side script into web pages viewed by other users.
-
Zombie Drone − A Zombie Drone is defined as a hi-jacked computer that is being used anonymously as a soldier or 'drone' for malicious activity, for example, distributing unwanted spam e-mails.
Ethical Hacking - Tools
在本章中,我们将简单探讨一些广泛用于防止黑客攻击和未经授权访问计算机或网络系统的著名工具。
In this chapter, we will discuss in brief some of famous tools that are widely used to prevent hacking and getting unauthorized access to a computer or network system.
NMAP
Nmap 代表网络映射器。它是一款开源工具,广泛用于网络发现和安全审核。Nmap 最初设计用于扫描大型网络,但它也可以同样很好地扫描单个主机。网络管理员还发现它对诸如网络清单、管理服务升级计划和监控主机或服务正常运行时间之类的任务很有用。
Nmap stands for Network Mapper. It is an open source tool that is used widely for network discovery and security auditing. Nmap was originally designed to scan large networks, but it can work equally well for single hosts. Network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime.
Nmap uses raw IP packets to determine −
-
what hosts are available on the network,
-
what services those hosts are offering,
-
what operating systems they are running on,
-
what type of firewalls are in use, and other such characteristics.
Nmap 可以在诸如 Windows、Mac OS X 和 Linux 等所有主流计算机操作系统中运行。
Nmap runs on all major computer operating systems such as Windows, Mac OS X, and Linux.
Metasploit
Metasploit 是最强大的漏洞利用工具之一。它是 Rapid7 的产品,并且其大部分资源可以在 www.metasploit.com 上找到。它分为两个版本 − commercial 和 free edition 。Matasploit 可以通过命令提示符或 Web UI 来使用。
Metasploit is one of the most powerful exploit tools. It’s a product of Rapid7 and most of its resources can be found at: www.metasploit.com. It comes in two versions − commercial and free edition. Matasploit can be used with command prompt or with Web UI.
使用 Metasploit,你可以执行以下操作:
With Metasploit, you can perform the following operations −
-
Conduct basic penetration tests on small networks
-
Run spot checks on the exploitability of vulnerabilities
-
Discover the network or import scan data
-
Browse exploit modules and run individual exploits on hosts
Burp Suit
Burp Suite 是一个流行的平台,广泛用于执行 Web 应用程序的安全测试。它拥有各种协同工作的工具,支持整个测试过程,包括从应用程序攻击面的初始映射和分析到查找和利用安全漏洞。
Burp Suite is a popular platform that is widely used for performing security testing of web applications. It has various tools that work in collaboration to support the entire testing process, from initial mapping and analysis of an application’s attack surface, through to finding and exploiting security vulnerabilities.
Burp 易于使用,并且为管理员提供了完全的控制权,以便将高级手动技术与自动化相结合以进行高效测试。Burp 可以轻松配置,并且包含一些功能,即使是最有经验的测试人员也能在工作中使用它们。
Burp is easy to use and provides the administrators full control to combine advanced manual techniques with automation for efficient testing. Burp can be easily configured and it contains features to assist even the most experienced testers with their work.
Angry IP Scanner
Angry IP 扫描器是一款轻量级的跨平台 IP 地址和端口扫描器。它可以在任何范围内扫描 IP 地址。它可以自由地复制,并且可以在任何地方使用。为了提高扫描速度,它采用了多线程方法,其中为每个扫描的 IP 地址创建了一个单独的扫描线程。
Angry IP scanner is a lightweight, cross-platform IP address and port scanner. It can scan IP addresses in any range. It can be freely copied and used anywhere. In order to increase the scanning speed, it uses multithreaded approach, wherein a separate scanning thread is created for each scanned IP address.
Angry IP 扫描仪只需对每个 IP 地址执行 ping 以检查它是否处于活动状态,然后解析其主机名,确定 MAC 地址,扫描端口等。有关每个主机的收集的数据量可以保存到 TXT、XML、CSV 或 IP-端口列表文件中。借助插件,Angry IP 扫描仪可以收集有关扫描的 IP 的任何信息。
Angry IP Scanner simply pings each IP address to check if it’s alive, and then, it resolves its hostname, determines the MAC address, scans ports, etc. The amount of gathered data about each host can be saved to TXT, XML, CSV, or IP-Port list files. With help of plugins, Angry IP Scanner can gather any information about scanned IPs.
Cain & Abel
Cain & Abel 是 Microsoft 操作系统的密码恢复工具。它通过采用下列任何一种方法帮助轻松恢复各种类型的密码 -
Cain & Abel is a password recovery tool for Microsoft Operating Systems. It helps in easy recovery of various kinds of passwords by employing any of the following methods −
-
sniffing the network,
-
cracking encrypted passwords using Dictionary, Brute-Force and Cryptanalysis attacks,
-
recording VoIP conversations,
-
decoding scrambled passwords,
-
recovering wireless network keys,
-
revealing password boxes,
-
uncovering cached passwords and analyzing routing protocols.
Cain & Abel 是一款非常实用的工具,适用于以下人群:安全顾问、专业渗透测试人员及打算出于道德原因使用该工具的人士。
Cain & Abel is a useful tool for security consultants, professional penetration testers and everyone else who plans to use it for ethical reasons.
Ettercap
Ettercap 的全称是 Ethernet Capture,它是一款用于针对中间人攻击的网络安全工具。它的功能包括嗅探活动连接、实时内容过滤以及其他许多有趣的小技巧。Ettercap 内置了网络和主机分析功能。它支持以主动和被动方式解析许多协议。
Ettercap stands for Ethernet Capture. It is a network security tool for Man-in-the-Middle attacks. It features sniffing of live connections, content filtering on the fly and many other interesting tricks. Ettercap has inbuilt features for network and host analysis. It supports active and passive dissection of many protocols.
你可以在所有流行的操作系统(例如 Windows、Linux 及 Mac OS X)上运行 Ettercap。
You can run Ettercap on all the popular operating systems such as Windows, Linux, and Mac OS X.
EtherPeek
EtherPeek 是一款非常棒的工具,它可以在多协议异构网络环境中简化网络分析。EtherPeek 是一款体积小巧(不足 2 MB)的工具,可以轻松地在数分钟内完成安装。
EtherPeek is a wonderful tool that simplifies network analysis in a multiprotocol heterogeneous network environment. EtherPeek is a small tool (less than 2 MB) that can be easily installed in a matter of few minutes.
EtherPeek 会主动嗅探网络上的流量数据包。在默认情况下,EtherPeek 支持以下协议:AppleTalk、IP、IP 地址解析协议 (ARP)、NetWare、TCP、UDP、NetBEUI 及 NBT 数据包。
EtherPeek proactively sniffs traffic packets on a network. By default, EtherPeek supports protocols such as AppleTalk, IP, IP Address Resolution Protocol (ARP), NetWare, TCP, UDP, NetBEUI, and NBT packets.
SuperScan
SuperScan 是一款非常强大的工具,网络管理员可以利用它来扫描 TCP 端口并解析主机名。它具有一个用户友好界面,可以用来:
SuperScan is a powerful tool for network administrators to scan TCP ports and resolve hostnames. It has a user friendly interface that you can use to −
-
Perform ping scans and port scans using any IP range.
-
Scan any port range from a built-in list or any given range.
-
View responses from connected hosts.
-
Modify the port list and port descriptions using the built in editor.
-
Merge port lists to build new ones.
-
Connect to any discovered open port.
-
Assign a custom helper application to any port.
QualysGuard
QualysGuard 包含了一套工具,可简化安全操作并降低合规成本。它可以按需提供重要的安全情报,并针对 IT 系统和 Web 应用程序自动执行审计、合规性和保护的全方位服务。
QualysGuard is an integrated suite of tools that can be utilized to simplify security operations and lower the cost of compliance. It delivers critical security intelligence on demand and automates the full spectrum of auditing, compliance and protection for IT systems and web applications.
QualysGuard 包含了一组可监控、检测和保护你的全球网络的工具。
QualysGuard includes a set of tools that can monitor, detect, and protect your global network.
WebInspect
WebInspect 是一款 Web 应用程序安全评估工具,它用于识别 Web 应用程序层中已知和未知的漏洞。
WebInspect is a web application security assessment tool that helps identify known and unknown vulnerabilities within the Web application layer.
它还可以帮助检查 Web 服务器是否配置正确,并尝试进行常见的 Web 攻击,例如参数注入、跨站点脚本编写、目录遍历等。
It can also help check that a Web server is configured properly, and attempts common web attacks such as parameter injection, cross-site scripting, directory traversal, and more.
LC4
LC4 之前称为 L0phtCrack 。它是一款密码审核与恢复应用程序。它用于测试密码强度和恢复丢失的 Microsoft Windows 密码(有时会使用字典、暴力破解和混合攻击)。
LC4 was formerly known as L0phtCrack. It is a password auditing and recovery application. It is used to test password strength and sometimes to recover lost Microsoft Windows passwords, by using dictionary, brute-force, and hybrid attacks.
LC4 会恢复 Windows 用户帐户密码,以簡化将用户迁移到另一个身份验证系统或访问密码丢失的帐户。
LC4 recovers Windows user account passwords to streamline migration of users to another authentication system or to access accounts whose passwords are lost.
LANguard Network Security Scanner
LANguard Network Scanner通过扫描连接的计算机并提供每个节点的信息来监控网络。你可以获得有关每个单独的操作系统的信息。
LANguard Network Scanner monitors a network by scanning connected machines and providing information about each node. You can obtain information about each individual operating system.
它还可以检测注册表问题,并设置 HTML 格式的报告。对于每台计算机,你可以列出 netbios 名称表、当前登录用户和 Mac 地址。
It can also detect registry issues and have a report set up in HTML format. For each computer, you can list the netbios name table, current logged-on user, and Mac address.
Network Stumbler
Network stumbler is a WiFi scanner and monitoring tool for Windows. It allows network professionals to detect WLANs. It is widely used by networking enthusiasts and hackers because it helps you find non-broadcasting wireless networks.
Network Stumbler can be used to verify if a network is well configured, its signal strength or coverage, and detect interference between one or more wireless networks. It can also be used to non-authorized connections.
ToneLoc
ToneLoc stands for Tone Locator. It was a popular war dialling computer program written for MS-DOS in the early 90’s. War dialling is a technique of using a modem to automatically scan a list of telephone numbers, usually dialling every number in a local area code.
恶意黑客利用产生的列表突破计算机安全,如猜测用户帐户或定位可作为入口点进入计算机或其他电子系统的调制解调器。
Malicious hackers use the resulting lists in breaching computer security - for guessing user accounts, or locating modems that might provide an entry-point into computer or other electronic systems.
安全人员可利用它检测公司电话网络上的未授权设备。
It can be used by security personnel to detect unauthorized devices on a company’s telephone network.
Ethical Hacking - Skills
作为一名道德黑客,你需要了解各种黑客技术,例如 −
As an ethical hacker, you will need to understand various hacking techniques such as −
-
Password guessing and cracking
-
Session hijacking
-
Session spoofing
-
Network traffic sniffing
-
Denial of Service attacks
-
Exploiting buffer overflow vulnerabilities
-
SQL injection
在本章中,我们将讨论你成为道德黑客专家所需的某些技能。
In this chapter, we will discuss some of the skills that you would require to become an expert in Ethical Hacking.
Basic Skills
计算机黑客既是一门科学,也是一门艺术。与任何其他专业知识一样,你需要付出大量努力才能获得知识并成为一名专家黑客。一旦你步入正轨,你需要付出更多努力来跟上最新技术、新漏洞和利用技术。
Computer Hacking is a Science as well as an Art. Like any other expertise, you need to put a lot of effort in order to acquire knowledge and become an expert hacker. Once you are on the track, you would need more effort to keep up-to-date with latest technologies, new vulnerabilities and exploitation techniques.
-
An ethical hacker must be a computer systems expert and needs to have very strong programming and computer networking skills.
-
An ethical hacker needs to have a lot of patience, persistence, and perseverance to try again and again and wait for the required result.
此外,道德黑客应该足够聪明来理解形势和其他用户的思维方式,以便运用社会工程漏洞。一名优秀的道德黑客也具备出色的问题解决能力。
Additionally, an ethical hacker should be smart enough to understand the situation and other users’ mind-set in order to apply social engineering exploits. A good ethical hacker has great problem-solving skills too.
Courses & Certifications
本教程提供了成为一名成功的道德黑客的基本准则。如果你想在这个领域脱颖而出,那么你可以选择参加以下课程和认证 −
This tutorial provides the basic guidelines to become a successful Ethical Hacker. If you want to excel in this field, then you might choose to pursue the following courses and certifications −
-
Obtain a bachelor’s degree in Computer Science or A+ Certificate to gain an understanding of the most common hardware and software technologies.
-
Get into a programmer’s role for a few years and then switch to get a tech support position.
-
Proceed to get network certifications like Network+ or CCNA and then security certifications like Security+, CISSP, or TICSA.
-
It is recommended that you get some work experience as a Network Engineer and System Administrator to understand networks and systems inside out.
-
Keep going through various books, tutorials and papers to understand various computer security aspects and take them as a challenge to secure your network and computer systems as network security engineer.
-
Study courses which cover creating Trojan horses, backdoors, viruses, and worms, denial of service (DoS) attacks, SQL injection, buffer overflow, session hijacking, and system hacking.
-
Master the art of penetration testing, footprinting and reconnaissance, and social engineering.
-
Finally go for a Certified Ethical Hacker (CEH) Certification.
GIAC(全球信息保证认证)和 Offensive Security Certified Professional (OSCP) 是额外的 IT 安全认证,它们将为您的个人资料增加很多价值。
GIAC (Global Information Assurance Certification) and Offensive Security Certified Professional (OSCP) are additional IT security certifications which will add a lot of value to your profile.
Final Note
您需要始终成为白帽黑客,这意味着您需要在既定的范围内工作。未经当局必需的许可,绝不行使或攻击任何计算机或网络。
You need to stay as a White Hat Hacker which means you need to work within given boundaries. Never intrude or attack any computer or network without a required permission from the authorities.
最后,强烈建议您不要参与可能毁掉您整个职业生涯的黑客攻击活动。
As a final note, it is highly recommended that you refrain from engaging yourself in black hat hacking which may spoil your entire career.
Ethical Hacking - Process
像所有好的项目一样,道德黑客攻击也有一组不同的阶段。它帮助黑客开展一场结构化的道德黑客攻击。
Like all good projects, ethical hacking too has a set of distinct phases. It helps hackers to make a structured ethical hacking attack.
不同的安全培训手册用不同的方式来解释道德黑客的过程,但对我来说,作为一个认证道德黑客,整个过程可以归类到以下六个阶段。
Different security training manuals explain the process of ethical hacking in different ways, but for me as a Certified Ethical Hacker, the entire process can be categorized into the following six phases.

Reconnaissance
侦察是攻击者使用主动或被动手段收集有关目标信息的一个阶段。在这个过程中广泛使用到的工具有 NMAP、Hping、Maltego 和 Google Dorks。
Reconnaissance is the phase where the attacker gathers information about a target using active or passive means. The tools that are widely used in this process are NMAP, Hping, Maltego, and Google Dorks.
Scanning
在这个过程中,攻击者开始主动探测目标机器或网络,以寻找可以被利用的漏洞。在这个过程中使用的工具有 Nessus、Nexpose 和 NMAP。
In this process, the attacker begins to actively probe a target machine or network for vulnerabilities that can be exploited. The tools used in this process are Nessus, Nexpose, and NMAP.
Gaining Access
在这个过程中,漏洞已被找到,你试图利用它来进入系统。在这个过程中使用到的主要工具是 Metasploit。
In this process, the vulnerability is located and you attempt to exploit it in order to enter into the system. The primary tool that is used in this process is Metasploit.
Maintaining Access
这是黑客已经获得进入系统访问权限的过程。在获得访问权限后,黑客安装了一些后门以便在未来需要访问这个已拥有系统时进入这个系统。在这个过程中,首选的工具是 Metasploit。
It is the process where the hacker has already gained access into a system. After gaining access, the hacker installs some backdoors in order to enter into the system when he needs access in this owned system in future. Metasploit is the preferred tool in this process.
Clearing Tracks
该过程实际上是一种不道德行为。它与删除在黑客过程中进行的所有活动的日志相关。
This process is actually an unethical activity. It has to do with the deletion of logs of all the activities that take place during the hacking process.
Reporting
报告是完成道德黑客攻击过程的最后一步。在这里,道德黑客根据他的发现和已完成的任务编写一份报告,例如使用的工具、成功率、发现的漏洞和利用进程。
Reporting is the last step of finishing the ethical hacking process. Here the Ethical Hacker compiles a report with his findings and the job that was done such as the tools used, the success rate, vulnerabilities found, and the exploit processes.
Quick Tip
这些过程不是标准的。在技术上,你可以根据自己擅长的,采用一系列不同的流程和工具。只要你能得到所需的结果,流程就最不重要。
The processes are not standard. You can adopt a set of different processes and tools according to your techniques that you are comfortable with. The process is of least significance as long as you are able to get the desired results.
Ethical Hacking - Reconnaissance
信息收集和了解目标系统是道德黑客攻击中的第一个过程。侦查是一组用来秘密发现和收集有关目标系统信息的流程和技术(足迹、扫描和枚举)。
Information Gathering and getting to know the target systems is the first process in ethical hacking. Reconnaissance is a set of processes and techniques (Footprinting, Scanning & Enumeration) used to covertly discover and collect information about a target system.
在侦查期间,道德黑客试图收集尽可能多的有关目标系统的信息,按照下面列出的七个步骤执行 −
During reconnaissance, an ethical hacker attempts to gather as much information about a target system as possible, following the seven steps listed below −
-
Gather initial information
-
Determine the network range
-
Identify active machines
-
Discover open ports and access points
-
Fingerprint the operating system
-
Uncover services on ports
-
Map the network
我们将在本教程的后续章节中详细讨论所有这些步骤。侦查分为两部分 − Active Reconnaissance 和 Passive Reconnaissance 。
We will discuss in detail all these steps in the subsequent chapters of this tutorial. Reconnaissance takes place in two parts − Active Reconnaissance and Passive Reconnaissance.
Active Reconnaissance
在该过程中,您将直接与计算机系统进行交互以获取信息。这些信息可能相关且准确。但如果您计划在未经允许的情况下进行主动侦察,则存在被检测到的风险。如果您被检测到,那么系统管理员可以对您采取严厉行动并追踪您后续的活动。
In this process, you will directly interact with the computer system to gain information. This information can be relevant and accurate. But there is a risk of getting detected if you are planning active reconnaissance without permission. If you are detected, then system admin can take severe action against you and trail your subsequent activities.
Ethical Hacking - Footprinting
足迹收集是一个侦察过程中的部分内容,用于收集目标计算机系统或网络的可能信息。足迹收集可以是 passive ,也可以是 active 。查看公司的网站是一个被动足迹收集的示例,而尝试通过社交工程学获取敏感信息是一个主动信息收集的示例。
Footprinting is a part of reconnaissance process which is used for gathering possible information about a target computer system or network. Footprinting could be both passive and active. Reviewing a company’s website is an example of passive footprinting, whereas attempting to gain access to sensitive information through social engineering is an example of active information gathering.
足迹收集基本上是黑客尽可能收集尽可能多的信息以找到入侵目标系统的方法或至少决定哪种类型的攻击更适合该目标的第一步。
Footprinting is basically the first step where hacker gathers as much information as possible to find ways to intrude into a target system or at least decide what type of attacks will be more suitable for the target.
在此阶段,黑客可以收集以下信息:
During this phase, a hacker can collect the following information −
-
Domain name
-
IP Addresses
-
Namespaces
-
Employee information
-
Phone numbers
-
E-mails
-
Job Information
在以下部分,我们将讨论如何提取有关连接到互联网的任何计算机系统或网络的基本且易于获取的信息。
In the following section, we will discuss how to extract the basic and easily accessible information about any computer system or network that is linked to the Internet.
Domain Name Information
您可以使用 http://www.whois.com/whois 网站获取有关域名信息的详细信息,包括其所有者、其注册商、注册日期、到期时间、名称服务器、所有者的联系信息等。
You can use http://www.whois.com/whois website to get detailed information about a domain name information including its owner, its registrar, date of registration, expiry, name server, owner’s contact information, etc.

以下是从 WHOIS 查询中提取的 www.tutorialspoint.com 的示例记录:
Here is a sample record of www.tutorialspoint.com extracted from WHOIS Lookup −

Finding IP Address
您可以在提示符处使用 ping 命令。此命令在 Windows 及 Linux 操作系统中均可用。以下是查找 tutorialspoint.com 的 IP 地址的示例:
You can use ping command at your prompt. This command is available on Windows as well as on Linux OS. Following is the example to find out the IP address of tutorialspoint.com
$ping tutorialspoint.com它将产生以下结果 −
It will produce the following result −
PING tutorialspoint.com (66.135.33.172) 56(84) bytes of data.
64 bytes from 66.135.33.172: icmp_seq = 1 ttl = 64 time = 0.028 ms
64 bytes from 66.135.33.172: icmp_seq = 2 ttl = 64 time = 0.021 ms
64 bytes from 66.135.33.172: icmp_seq = 3 ttl = 64 time = 0.021 ms
64 bytes from 66.135.33.172: icmp_seq = 4 ttl = 64 time = 0.021 msFinding Hosting Company
获得网站地址后,您可以使用 [role="bare"] [role="bare"]https://www.ip2location.com/ip2location.com 网站来获取更多详细信息。以下是查找 IP 地址详细信息的示例:
Once you have the website address, you can get further detail by using [role="bare"]https://www.ip2location.com/ip2location.com website. Following is the example to find out the details of an IP address −

此处,ISP 行会向您提供有关托管公司的详细信息,因为 IP 地址通常仅由托管公司提供。
Here the ISP row gives you the detail about the hosting company because IP addresses are usually provided by hosting companies only.
Quick Fix
如果计算机系统或网络直接连接到互联网,则无法隐藏 IP 地址及相关信息,例如托管公司、其位置、ISP 等。如果您有一个包含非常敏感数据的服务器,建议将其保留在安全代理后面,以便黑客无法获取您实际服务器的确切详细信息。这样,任何潜在的黑客都将很难直接访问您的服务器。
If a computer system or network is linked with the Internet directly, then you cannot hide the IP address and the related information such as the hosting company, its location, ISP, etc. If you have a server containing very sensitive data, then it is recommended to keep it behind a secure proxy so that hackers cannot get the exact details of your actual server. This way, it will be difficult for any potential hacker to reach your server directly.
隐藏您的系统 IP 以及最终所有关联信息的另一种有效方法是通过虚拟专用网络 (VPN)。如果您配置了 VPN,则整个流量将通过 VPN 网络路由,因此您的 ISP 分配的真实 IP 地址始终被隐藏。
Another effective way of hiding your system IP and ultimately all the associated information is to go through a Virtual Private Network (VPN). If you configure a VPN, then the whole traffic routes through the VPN network, so your true IP address assigned by your ISP is always hidden.
IP Address Ranges
小型站点可能与其关联单个 IP 地址,但较大的网站通常具有多个用于提供不同域名和子域名的 IP 地址。
Small sites may have a single IP address associated with them, but larger websites usually have multiple IP addresses serving different domains and sub-domains.
你可以使用 American Registry for Internet Numbers (ARIN). 获取分配给特定公司的 IP 地址范围。
You can obtain a range of IP addresses assigned to a particular company using American Registry for Internet Numbers (ARIN).

你可以在高亮的搜索框中输入公司名称,找到分配给该公司所有 IP 地址的列表。
You can enter company name in the highlighted search box to find out a list of all the assigned IP addresses to that company.
History of the Website
使用 www.archive.org 获取任何网站的完整历史非常容易。
It is very easy to get a complete history of any website using www.archive.org.

可以在搜索框中输入一个域名,找到该网站在给定时间点的外观,以及在不同的日期里网站上有哪些页面可用。
You can enter a domain name in the search box to find out how the website was looking at a given point of time and what were the pages available on the website on different dates.

Quick Fix
尽管将网站放在归档数据库中有一些优势,但如果你不希望任何人看到你的网站在不同阶段是如何发展的,那么可以请求 archive.org 删除网站的历史记录。
Though there are some advantages of keeping your website in an archive database, but if you do not like anybody to see how your website progressed through different stages, then you can request archive.org to delete the history of your website.
Ethical Hacking - Fingerprinting
道德黑客中的术语 OS 指纹识别是指用来确定远程计算机上运行什么操作系统的任何方法。这可能是−
The term OS fingerprinting in Ethical Hacking refers to any method used to determine what operating system is running on a remote computer. This could be −
-
Active Fingerprinting − Active fingerprinting is accomplished by sending specially crafted packets to a target machine and then noting down its response and analyzing the gathered information to determine the target OS. In the following section, we have given an example to explain how you can use NMAP tool to detect the OS of a target domain.
-
Passive Fingerprinting − Passive fingerprinting is based on sniffer traces from the remote system. Based on the sniffer traces (such as Wireshark) of the packets, you can determine the operating system of the remote host.
我们有以下四个重要元素,我们将在其中查看这些元素以确定操作系统−
We have the following four important elements that we will look at to determine the operating system −
-
TTL − What the operating system sets the Time-To-Live on the outbound packet.
-
Window Size − What the operating system sets the Window Size at.
-
DF − Does the operating system set the Don’t Fragment bit.
-
TOS − Does the operating system set the Type of Service, and if so, at what.
通过分析数据包的这些因素,你能确定远程操作系统。此系统并非 100% 准确,且适用于某些操作系统,而不适用于其他操作系统。
By analyzing these factors of a packet, you may be able to determine the remote operating system. This system is not 100% accurate, and works better for some operating systems than others.
Basic Steps
在攻击系统之前,你必须知道是哪些操作系统承载网站。一旦知道了目标操作系统,就很容易确定可能存在哪些漏洞以利用目标系统。
Before attacking a system, it is required that you know what operating system is hosting a website. Once a target OS is known, then it becomes easy to determine which vulnerabilities might be present to exploit the target system.
下面是一个简单的 nmap 命令,可以用来识别用于承载网站的操作系统,以及与域名相关的所有已打开端口,即 IP 地址。
Below is a simple nmap command which can be used to identify the operating system serving a website and all the opened ports associated with the domain name, i.e., the IP address.
$nmap -O -v tutorialspoint.com它将向你展示有关给定域名或 IP 地址的以下敏感信息:
It will show you the following sensitive information about the given domain name or IP address −
Starting Nmap 5.51 ( http://nmap.org ) at 2015-10-04 09:57 CDT
Initiating Parallel DNS resolution of 1 host. at 09:57
Completed Parallel DNS resolution of 1 host. at 09:57, 0.00s elapsed
Initiating SYN Stealth Scan at 09:57
Scanning tutorialspoint.com (66.135.33.172) [1000 ports]
Discovered open port 22/tcp on 66.135.33.172
Discovered open port 3306/tcp on 66.135.33.172
Discovered open port 80/tcp on 66.135.33.172
Discovered open port 443/tcp on 66.135.33.172
Completed SYN Stealth Scan at 09:57, 0.04s elapsed (1000 total ports)
Initiating OS detection (try #1) against tutorialspoint.com (66.135.33.172)
Retrying OS detection (try #2) against tutorialspoint.com (66.135.33.172)
Retrying OS detection (try #3) against tutorialspoint.com (66.135.33.172)
Retrying OS detection (try #4) against tutorialspoint.com (66.135.33.172)
Retrying OS detection (try #5) against tutorialspoint.com (66.135.33.172)
Nmap scan report for tutorialspoint.com (66.135.33.172)
Host is up (0.000038s latency).
Not shown: 996 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
443/tcp open https
3306/tcp open mysql
TCP/IP fingerprint:
OS:SCAN(V=5.51%D=10/4%OT=22%CT=1%CU=40379%PV=N%DS=0%DC=L%G=Y%TM=56113E6D%P=
OS:x86_64-redhat-linux-gnu)SEQ(SP=106%GCD=1%ISR=109%TI=Z%CI=Z%II=I%TS=A)OPS
OS:(O1=MFFD7ST11NW7%O2=MFFD7ST11NW7%O3=MFFD7NNT11NW7%O4=MFFD7ST11NW7%O5=MFF
OS:D7ST11NW7%O6=MFFD7ST11)WIN(W1=FFCB%W2=FFCB%W3=FFCB%W4=FFCB%W5=FFCB%W6=FF
OS:CB)ECN(R=Y%DF=Y%T=40%W=FFD7%O=MFFD7NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A
OS:=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%
OS:Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=
OS:A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=
OS:Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%
OS:T=40%CD=S)如果你没有在 Linux 系统上安装 nmap 命令,那么你可以使用以下 yum 命令安装它:
If you do not have nmap command installed on your Linux system, then you can install it using the following yum command −
$yum install nmap你可以仔细查看 nmap 命令来检查和了解与系统相关并保护其免遭恶意攻击的不同功能。
You can go through nmap command in detail to check and understand the different features associated with a system and secure it against malicious attacks.
Port Scanning
我们刚刚看到 nmap 命令给出的信息。此命令会列出给定服务器上所有打开的端口。
We have just seen information given by nmap command. This command lists down all the open ports on a given server.
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
443/tcp open https
3306/tcp open mysql你还可以使用以下命令检查是否打开了特定的端口:
You can also check if a particular port is opened or not using the following command −
$nmap -sT -p 443 tutorialspoint.com它将产生以下结果 −
It will produce the following result −
Starting Nmap 5.51 ( http://nmap.org ) at 2015-10-04 10:19 CDT
Nmap scan report for tutorialspoint.com (66.135.33.172)
Host is up (0.000067s latency).
PORT STATE SERVICE
443/tcp open https
Nmap done: 1 IP address (1 host up) scanned in 0.04 seconds一旦黑客知道打开的端口,那么他就可以通过打开的端口计划不同的攻击技术。
Once a hacker knows about open ports, then he can plan different attack techniques through the open ports.
Ping Sweep
Ping 扫描是一种网络扫描技术,你可以使用它来确定 IP 地址范围内的哪些 IP 地址映射到活动主机。Ping 扫描也称为 ICMP sweep 。
A ping sweep is a network scanning technique that you can use to determine which IP address from a range of IP addresses map to live hosts. Ping Sweep is also known as ICMP sweep.
你可以对 Ping 扫描使用 fping 命令。此命令是一个类似 ping 的程序,它使用因特网控制消息协议 (ICMP) 回声请求来确定主机是否已启动。
You can use fping command for ping sweep. This command is a ping-like program which uses the Internet Control Message Protocol (ICMP) echo request to determine if a host is up.
fping 不同于 ping ,因为你可以在命令行上指定任意数量的主机,或指定包含要 ping 的主机列表的文件。如果主机在某个时间限制和/或重试限制内没有响应,它将被认为不可达。
fping is different from ping in that you can specify any number of hosts on the command line, or specify a file containing the lists of hosts to ping. If a host does not respond within a certain time limit and/or retry limit, it will be considered unreachable.
Quick Fix
要在网络上禁用 ping 扫描,你可以阻止来自外部来源的 ICMP ECHO 请求。你可以使用以下命令来完成此操作,这将在 iptable 中创建一个防火墙规则。
To disable ping sweeps on a network, you can block ICMP ECHO requests from outside sources. This can be done using the following command which will create a firewall rule in iptable.
$iptables -A OUTPUT -p icmp --icmp-type echo-request -j DROPDNS Enumeration
域名服务器 (DNS) 像地图或地址簿。事实上,它就像一个分布式数据库,用于将 IP 地址 192.111.1.120 转换为名称 www.example.com, 反之亦然。
Domain Name Server (DNS) is like a map or an address book. In fact, it is like a distributed database which is used to translate an IP address 192.111.1.120 to a name www.example.com and vice versa.
DNS 枚举是查找所有 DNS 服务器及其对应记录的过程。其目的是在发起攻击之前尽可能收集有关目标的有趣详细信息。
DNS enumeration is the process of locating all the DNS servers and their corresponding records for an organization. The idea is to gather as much interesting details as possible about your target before initiating an attack.
你可以在 Linux 上使用 nslookup 命令来获取 DNS 和主机相关信息。此外,你可以使用以下 DNSenum 脚本来获取有关域名的详细信息:
You can use nslookup command available on Linux to get DNS and host-related information. In addition, you can use the following DNSenum script to get detailed information about a domain −
DNSenum 脚本可以执行以下重要操作 −
DNSenum script can perform the following important operations −
-
Get the host’s addresses
-
Get the nameservers
-
Get the MX record
-
Perform axfr queries on nameservers
-
Get extra names and subdomains via Google scraping
-
Brute force subdomains from file can also perform recursion on subdomain that has NS records
-
Calculate C class domain network ranges and perform whois queries on them
-
Perform reverse lookups on netranges
Quick Fix
DNS 枚举没有快速修复程序,并且它确实超出了本教程的范围。防止 DNS 枚举是一个重大挑战。
DNS Enumeration does not have a quick fix and it is really beyond the scope of this tutorial. Preventing DNS Enumeration is a big challenge.
如果您的 DNS 未以安全的方式配置,网络和组织的大量敏感信息可能会泄露出去,并且不受信任的 Internet 用户可能会执行 DNS 区域传输。
If your DNS is not configured in a secure way, it is possible that lots of sensitive information about the network and organization can go outside and an untrusted Internet user can perform a DNS zone transfer.
Ethical Hacking - Sniffing
嗅探是使用嗅探工具监控和捕获通过给定网络的所有数据包的过程。这是一种“窃听电话线”并了解对话的形式。它也被称为 wiretapping 应用于计算机网络。
Sniffing is the process of monitoring and capturing all the packets passing through a given network using sniffing tools. It is a form of “tapping phone wires” and get to know about the conversation. It is also called wiretapping applied to the computer networks.
如果一组企业交换机端口已打开,就有很大的可能性,他们的一名员工可以嗅探网络的全部流量。任何在相同物理位置的人都可以使用以太网电缆连接到网络,或以无线方式连接到该网络并嗅探全部流量。
There is so much possibility that if a set of enterprise switch ports is open, then one of their employees can sniff the whole traffic of the network. Anyone in the same physical location can plug into the network using Ethernet cable or connect wirelessly to that network and sniff the total traffic.
换句话说,嗅探使您可以查看各种流量,包括受保护和不受保护的流量。在条件合适且实施了正确的协议时,攻击方有可能收集可用于进一步攻击或给网络或系统所有者造成其他问题的信息。
In other words, Sniffing allows you to see all sorts of traffic, both protected and unprotected. In the right conditions and with the right protocols in place, an attacking party may be able to gather information that can be used for further attacks or to cause other issues for the network or system owner.
What can be sniffed?
人们可以从网络中嗅探以下敏感信息——
One can sniff the following sensitive information from a network −
-
Email traffic
-
FTP passwords
-
Web traffics
-
Telnet passwords
-
Router configuration
-
Chat sessions
-
DNS traffic
How it works
嗅探器通常将系统的 NIC 转到 promiscuous mode ,以便它监听在其网段上传输的所有数据。
A sniffer normally turns the NIC of the system to the promiscuous mode so that it listens to all the data transmitted on its segment.
混杂模式是指以太网硬件(特别是网络接口卡 (NIC))的独特方式,它允许 NIC 接收网络上的所有流量,即使该流量不是针对此 NIC 的。默认情况下,NIC 会忽略所有未发送给它的流量,这是通过将以太网数据包的目标地址与设备的硬件地址(也称为 MAC)进行比较来完成的。虽然这对于网络来说很有意义,但是非混杂模式使得难以使用网络监视和分析软件来诊断连接问题或流量利用率。
Promiscuous mode refers to the unique way of Ethernet hardware, in particular, network interface cards (NICs), that allows an NIC to receive all traffic on the network, even if it is not addressed to this NIC. By default, a NIC ignores all traffic that is not addressed to it, which is done by comparing the destination address of the Ethernet packet with the hardware address (a.k.a. MAC) of the device. While this makes perfect sense for networking, non-promiscuous mode makes it difficult to use network monitoring and analysis software for diagnosing connectivity issues or traffic accounting.
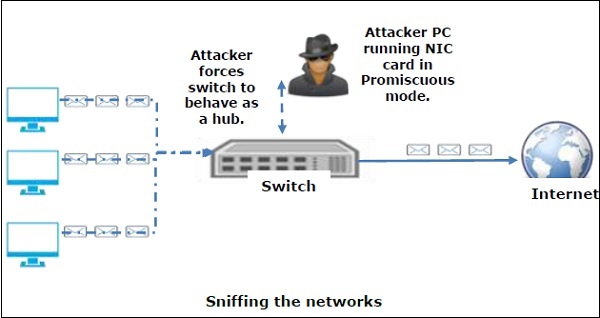
嗅探器可以通过解码数据包中封装的信息,持续监视通过网卡传输到计算机的所有流量。
A sniffer can continuously monitor all the traffic to a computer through the NIC by decoding the information encapsulated in the data packets.
Types of Sniffing
嗅探本质上可分为主动或被动。
Sniffing can be either Active or Passive in nature.
Passive Sniffing
在被动嗅探中,流量被锁定,但不会以任何方式被改变。被动嗅探只允许监听。它适用于集线器设备。在集线器设备上,流量会被发送到所有端口。在一个使用集线器连接系统的网络中,网络上的所有主机都可以看到流量。因此,攻击者可以轻松捕获流量。
In passive sniffing, the traffic is locked but it is not altered in any way. Passive sniffing allows listening only. It works with Hub devices. On a hub device, the traffic is sent to all the ports. In a network that uses hubs to connect systems, all hosts on the network can see the traffic. Therefore, an attacker can easily capture traffic going through.
好消息是,如今集线器几乎已经过时了。大多数现代网络使用交换机。因此,被动嗅探不再有效。
The good news is that hubs are almost obsolete nowadays. Most modern networks use switches. Hence, passive sniffing is no more effective.
Active Sniffing
在主动嗅探中,流量不仅被锁定和监控,而且可能会根据攻击者的决定以某种方式被改变。主动嗅探用于嗅探基于交换机的网络。它涉及向目标网络注入 address resolution packets (ARP),以在交换机 content addressable memory (CAM)表中泛洪。CAM 会跟踪每个主机连接到哪个端口。
In active sniffing, the traffic is not only locked and monitored, but it may also be altered in some way as determined by the attack. Active sniffing is used to sniff a switch-based network. It involves injecting address resolution packets (ARP) into a target network to flood on the switch content addressable memory (CAM) table. CAM keeps track of which host is connected to which port.
以下是主动嗅探技术——
Following are the Active Sniffing Techniques −
-
MAC Flooding
-
DHCP Attacks
-
DNS Poisoning
-
Spoofing Attacks
-
ARP Poisoning
Protocols which are affected
诸如久经考验的 TCP/IP 等协议在设计时从未考虑安全性,因此对潜在攻击者几乎没有抵抗力。几条规则很容易被嗅探 −
Protocols such as the tried and true TCP/IP were never designed with security in mind and therefore do not offer much resistance to potential intruders. Several rules lend themselves to easy sniffing −
-
HTTP − It is used to send information in the clear text without any encryption and thus a real target.
-
SMTP (Simple Mail Transfer Protocol) − SMTP is basically utilized in the transfer of emails. This protocol is efficient, but it does not include any protection against sniffing.
-
NNTP (Network News Transfer Protocol)− It is used for all types of communications, but its main drawback is that data and even passwords are sent over the network as clear text.
-
POP (Post Office Protocol) − POP is strictly used to receive emails from the servers. This protocol does not include protection against sniffing because it can be trapped.
-
FTP (File Transfer Protocol) − FTP is used to send and receive files, but it does not offer any security features. All the data is sent as clear text that can be easily sniffed.
-
IMAP (Internet Message Access Protocol) − IMAP is same as SMTP in its functions, but it is highly vulnerable to sniffing.
-
Telnet − Telnet sends everything (usernames, passwords, keystrokes) over the network as clear text and hence, it can be easily sniffed.
嗅探器并不是只能让你查看实时流量的简单工具。如果你真的想要对每个数据包进行分析,请保存捕获内容并在时间允许时对其进行查看。
Sniffers are not the dumb utilities that allow you to view only live traffic. If you really want to analyze each packet, save the capture and review it whenever time allows.
Hardware Protocol Analyzers
在我们进一步了解嗅探器之前,讨论 hardware protocol analyzers 很重要。这些设备会在硬件级别插入网络,并且可以监视流量而不会对其进行操纵。
Before we go into further details of sniffers, it is important that we discuss about hardware protocol analyzers. These devices plug into the network at the hardware level and can monitor traffic without manipulating it.
-
Hardware protocol analyzers are used to monitor and identify malicious network traffic generated by hacking software installed in the system.
-
They capture a data packet, decode it, and analyze its content according to certain rules.
-
Hardware protocol analyzers allow attackers to see individual data bytes of each packet passing through the cable.
由于在许多情况下成本非常高,因此大多数道德黑客无法轻易获得这些硬件设备。
These hardware devices are not readily available to most ethical hackers due to their enormous cost in many cases.
Lawful Interception
合法截取(LI)被定义为合法获取通信网络数据(如电话呼叫或电子邮件)的途径。LI 始终必须为了分析或证据的目的而追求合法权限。因此,法律截取是一种安全流程,其中网络运营商或服务供应商允许执法人员访问个人或组织的私人通信。
Lawful Interception (LI) is defined as legally sanctioned access to communications network data such as telephone calls or email messages. LI must always be in pursuance of a lawful authority for the purpose of analysis or evidence. Therefore, LI is a security process in which a network operator or service provider gives law enforcement officials permission to access private communications of individuals or organizations.
几乎所有国家都起草并颁布了法规来规范合法截取程序;标准化组织正在制定 LI 技术规范。通常,LI 活动是为了基础设施保护和网络安全的目的而进行。然而,除非另有禁止,私人网络基础设施的运营商可以在其自己的网络内保留 LI 功能,作为固有权利。
Almost all countries have drafted and enacted legislation to regulate lawful interception procedures; standardization groups are creating LI technology specifications. Usually, LI activities are taken for the purpose of infrastructure protection and cyber security. However, operators of private network infrastructures can maintain LI capabilities within their own networks as an inherent right, unless otherwise prohibited.
LI 以前称为 wiretapping ,并且自电子通信出现以来就已存在。
LI was formerly known as wiretapping and has existed since the inception of electronic communications.
Ethical Hacking - Sniffing Tools
在网络上进行嗅探有很多可用的工具,它们都具有自己的特性来帮助黑客分析流量并获取信息。嗅探工具是非常常见的应用程序。我们在此列出了一些有趣的工具:
There are so many tools available to perform sniffing over a network, and they all have their own features to help a hacker analyze traffic and dissect the information. Sniffing tools are extremely common applications. We have listed here some of the interesting ones −
-
BetterCAP − BetterCAP is a powerful, flexible and portable tool created to perform various types of MITM attacks against a network, manipulate HTTP, HTTPS and TCP traffic in real-time, sniff for credentials, and much more.
-
Ettercap − Ettercap is a comprehensive suite for man-in-the-middle attacks. It features sniffing of live connections, content filtering on the fly and many other interesting tricks. It supports active and passive dissection of many protocols and includes many features for network and host analysis.
-
Wireshark − It is one of the most widely known and used packet sniffers. It offers a tremendous number of features designed to assist in the dissection and analysis of traffic.
-
Tcpdump − It is a well-known command-line packet analyzer. It provides the ability to intercept and observe TCP/IP and other packets during transmission over the network. Available at www.tcpdump.org.
-
WinDump − A Windows port of the popular Linux packet sniffer tcpdump, which is a command-line tool that is perfect for displaying header information.
-
OmniPeek − Manufactured by WildPackets, OmniPeek is a commercial product that is the evolution of the product EtherPeek.
-
Dsniff − A suite of tools designed to perform sniffing with different protocols with the intent of intercepting and revealing passwords. Dsniff is designed for Unix and Linux platforms and does not have a full equivalent on the Windows platform.
-
EtherApe − It is a Linux/Unix tool designed to display graphically a system’s incoming and outgoing connections.
-
MSN Sniffer − It is a sniffing utility specifically designed for sniffing traffic generated by the MSN Messenger application.
-
NetWitness NextGen − It includes a hardware-based sniffer, along with other features, designed to monitor and analyze all traffic on a network. This tool is used by the FBI and other law enforcement agencies.
潜在的黑客可以使用这些嗅探工具中的任何一个来分析网络流量并获取信息。
A potential hacker can use any of these sniffing tools to analyze traffic on a network and dissect information.
Ethical Hacking - ARP Poisoning
地址解析协议 (ARP) 是一种无状态协议,用于将 IP 地址解析为计算机的 MAC 地址。网络上需要进行通信的所有网络设备都会在系统中广播 ARP 查询,以找出其他计算机的 MAC 地址。ARP 欺骗也称为 ARP Spoofing 。
Address Resolution Protocol (ARP) is a stateless protocol used for resolving IP addresses to machine MAC addresses. All network devices that need to communicate on the network broadcast ARP queries in the system to find out other machines’ MAC addresses. ARP Poisoning is also known as ARP Spoofing.
以下是 ARP 的工作原理:
Here is how ARP works −
-
When one machine needs to communicate with another, it looks up its ARP table.
-
If the MAC address is not found in the table, the ARP_request is broadcasted over the network.
-
All machines on the network will compare this IP address to MAC address.
-
If one of the machines in the network identifies this address, then it will respond to the ARP_request with its IP and MAC address.
-
The requesting computer will store the address pair in its ARP table and communication will take place.
What is ARP Spoofing?
可以伪造 ARP 数据包以将数据发送到攻击者的计算机。
ARP packets can be forged to send data to the attacker’s machine.
-
ARP spoofing constructs a large number of forged ARP request and reply packets to overload the switch.
-
The switch is set in forwarding mode and after the ARP table is flooded with spoofed ARP responses, the attackers can sniff all network packets.
攻击者用伪造的条目随机填充目标计算机的 ARP 缓存,这也称为 poisoning 。ARP 欺骗使用中间人访问来污染网络。
Attackers flood a target computer ARP cache with forged entries, which is also known as poisoning. ARP poisoning uses Man-in-the-Middle access to poison the network.
What is MITM?
中间人攻击(缩写为 MITM、MitM、MIM、MiM、MITMA)暗示一种主动攻击,其中 adversaries 冒充用户,通过在受害者之间创建连接并发送他们之间的消息来进行攻击。在这种情况下,受害者认为他们在彼此通信,但实际上,恶意行为者控制着通信。
The Man-in-the-Middle attack (abbreviated MITM, MitM, MIM, MiM, MITMA) implies an active attack where the adversary impersonates the user by creating a connection between the victims and sends messages between them. In this case, the victims think that they are communicating with each other, but in reality, the malicious actor controls the communication.

存在第三人来控制和监视两方之间的通信流量。诸如 SSL 等一些协议有助于阻止这种类型的攻击。
A third person exists to control and monitor the traffic of communication between two parties. Some protocols such as SSL serve to prevent this type of attack.
ARP Poisoning − Exercise
在本练习中,我们在安装了 Kali Linux 和 Ettercap 工具以嗅探 LAN 中本地流量的 VMware 工作站中,使用 BetterCAP 在 LAN 环境中执行 ARP 欺骗。
In this exercise, we have used BetterCAP to perform ARP poisoning in LAN environment using VMware workstation in which we have installed Kali Linux and Ettercap tool to sniff the local traffic in LAN.
For this exercise, you would need the following tools −
-
VMware workstation
-
Kali Linux or Linux Operating system
-
Ettercap Tool
-
LAN connection
Note − This attack is possible in wired and wireless networks. You can perform this attack in local LAN.
Step 1 − 安装 VMware 工作站并安装 Kali Linux 操作系统。
Step 1 − Install the VMware workstation and install the Kali Linux operating system.
Step 2 − 使用用户名和密码“root, toor”登录到 Kali Linux。
Step 2 − Login into the Kali Linux using username pass “root, toor”.
Step 3 − 确保已连接到本地 LAN,并通过在终端中键入命令 ifconfig 来检查 IP 地址。
Step 3 − Make sure you are connected to local LAN and check the IP address by typing the command ifconfig in the terminal.

Step 4 - 打开终端并键入“Ettercap –G”以启动 Ettercap 的图形化版本。
Step 4 − Open up the terminal and type “Ettercap –G” to start the graphical version of Ettercap.

Step 5 - 现在点击菜单栏中的“嗅探”标签并选择“统一嗅探”,然后点击“好”选择接口。我们将使用“eth0”,这意味着以太网连接。
Step 5 − Now click the tab “sniff” in the menu bar and select “unified sniffing” and click OK to select the interface. We are going to use “eth0” which means Ethernet connection.

Step 6 - 现在点击菜单栏中的“主机”标签,然后点击“扫描主机”。它将开始扫描整个网络以查找活动主机。
Step 6 − Now click the “hosts” tab in the menu bar and click “scan for hosts”. It will start scanning the whole network for the alive hosts.
Step 7 - 接下来,单击“hosts”选项卡并选择“hosts list”以查看网络中可用的主机数量。此列表还包括默认网关地址。我们在选择目标时必须小心。
Step 7 − Next, click the “hosts” tab and select “hosts list” to see the number of hosts available in the network. This list also includes the default gateway address. We have to be careful when we select the targets.

Step 8 - 现在我们必须选择目标。在 MITM 中,我们的目标是主机,并且路由将是转发流量的路由器地址。在 MITM 攻击中,攻击者会拦截网络并嗅探数据包。所以,我们将受害者作为“目标 1”添加进去,并将路由器地址作为“目标 2”添加进去。
Step 8 − Now we have to choose the targets. In MITM, our target is the host machine, and the route will be the router address to forward the traffic. In an MITM attack, the attacker intercepts the network and sniffs the packets. So, we will add the victim as “target 1” and the router address as “target 2.”
在 VMware 环境中,默认网关将始终以“2”结尾,因为“1”已分配给物理机。
In VMware environment, the default gateway will always end with “2” because “1” is assigned to the physical machine.
Step 9 − In this scenario, our target is “192.168.121.129” and the router is “192.168.121.2”. So we will add target 1 as victim IP and target 2 as router IP.

Step 10 − Now click on “MITM” and click “ARP poisoning”. Thereafter, check the option “Sniff remote connections” and click OK.

Step 11 − Click “start” and select “start sniffing”. This will start ARP poisoning in the network which means we have enabled our network card in “promiscuous mode” and now the local traffic can be sniffed.
Note - 我们仅允许使用 Ettercap 进行 HTTP 嗅探,因此不要指望使用此进程嗅探 HTTPS 数据包。
Note − We have allowed only HTTP sniffing with Ettercap, so don’t expect HTTPS packets to be sniffed with this process.
Step 12 - 现在是查看结果的时候了;如果受害者登录了某些网站。你可以在 Ettercap 的工具栏中查看结果。
Step 12 − Now it’s time to see the results; if our victim logged into some websites. You can see the results in the toolbar of Ettercap.

以下是嗅探是如何运作的。您一定已经明白了,只需启用 ARP 欺骗就可以轻松获得 HTTP 凭据。
This is how sniffing works. You must have understood how easy it is to get the HTTP credentials just by enabling ARP poisoning.
ARP 欺骗有可能会给公司环境造成巨大损失。这就是任命道德黑客来保护网络的地方。
ARP Poisoning has the potential to cause huge losses in company environments. This is the place where ethical hackers are appointed to secure the networks.
与 ARP 欺骗类似,还有其他攻击,例如 MAC 泛洪、MAC 欺骗、DNS 欺骗和 ICMP 欺骗,它们都可能给网络造成重大损失。
Like ARP poisoning, there are other attacks such as MAC flooding, MAC spoofing, DNS poisoning, ICMP poisoning, etc. that can cause significant loss to a network.
在下一章,我们将会讨论另一种称为 DNS poisoning 的攻击类型。
In the next chapter, we will discuss another type of attack known as DNS poisoning.
Ethical Hacking - DNS Poisoning
DNS 欺骗是一种欺骗 DNS 服务器,使其确信它已收到真实信息的技术,而实际上它并未收到。这将导致在 DNS 级别替换错误的 IP 地址,在那里 Web 地址被转换为数字 IP 地址。它允许攻击者用服务器控件的 IP 地址替换给定 DNS 服务器上目标网站的 IP 地址条目。攻击者可以创建可能包含恶意内容的服务器假 DNS 条目,名称与该服务器相同。
DNS Poisoning is a technique that tricks a DNS server into believing that it has received authentic information when, in reality, it has not. It results in the substitution of false IP address at the DNS level where web addresses are converted into numeric IP addresses. It allows an attacker to replace IP address entries for a target site on a given DNS server with IP address of the server controls. An attacker can create fake DNS entries for the server which may contain malicious content with the same name.
例如,用户键入 www.google.com,但用户会被发送到另一个欺诈网站,而不是被定向到 Google 服务器。正如我们所理解的,DNS 欺骗用于将用户重定向到由攻击者管理的虚假页面。
For instance, a user types www.google.com, but the user is sent to another fraud site instead of being directed to Google’s servers. As we understand, DNS poisoning is used to redirect the users to fake pages which are managed by the attackers.
DNS Poisoning − Exercise
让我们使用相同的工具 Ettercap 对 DNS 欺骗进行练习。
Let’s do an exercise on DNS poisoning using the same tool, Ettercap.
DNS 欺骗非常类似于 ARP 欺骗。要启动 DNS 欺骗,您必须从我们在上一章中已经讨论过的 ARP 欺骗开始。我们将使用 Ettercap 中已经存在的 DNS spoof 插件。
DNS Poisoning is quite similar to ARP Poisoning. To initiate DNS poisoning, you have to start with ARP poisoning, which we have already discussed in the previous chapter. We will use DNS spoof plugin which is already there in Ettercap.
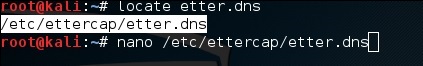
Step 1 − 打开终端并键入“nano etter.dns”。此文件包含由 Ettercap 用于解析域名地址的所有 DNS 地址的条目。在此文件中,我们将添加 Facebook 的一个假条目。如果有人想要打开 Facebook,他将被重定向到另一个网站。
Step 1 − Open up the terminal and type “nano etter.dns”. This file contains all entries for DNS addresses which is used by Ettercap to resolve the domain name addresses. In this file, we will add a fake entry of “Facebook”. If someone wants to open Facebook, he will be redirected to another website.
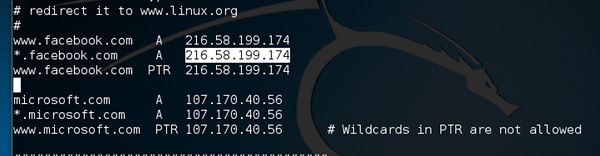
Step 2 − 现在在“重定向到 www.linux.org” 字样下插入条目。请参见以下示例 −
Step 2 − Now insert the entries under the words “Redirect it to www.linux.org”. See the following example −
Step 3 - 现在保存此文件并保存文件退出。使用“ctrl+x”保存文件。
Step 3 − Now save this file and exit by saving the file. Use “ctrl+x” to save the file.
Step 4 - 此后,整个过程都相同,开始 ARP 中毒。启动 ARP 中毒后,单击菜单栏中的“插件”并选择“dns_spoof”插件。
Step 4 − After this, the whole process is same to start ARP poisoning. After starting ARP poisoning, click on “plugins” in the menu bar and select “dns_spoof” plugin.
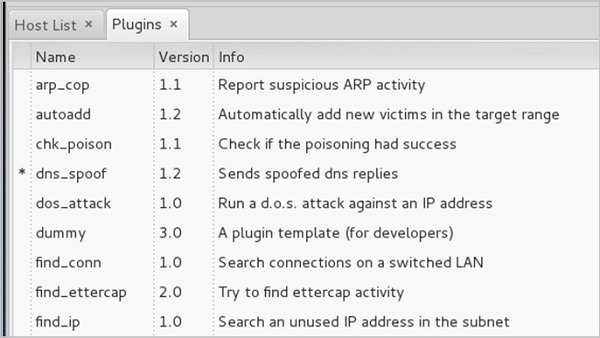
Step 5 - 激活 DNS_spoof 后,您将在结果中看到,每当有人在其浏览器中键入 facebook.com 时,它将开始向 Google IP 进行欺骗。
Step 5 − After activating the DNS_spoof, you will see in the results that facebook.com will start spoofed to Google IP whenever someone types it in his browser.
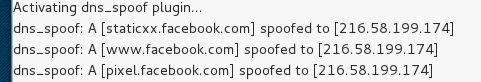
这意味着用户在其浏览器中获取 Google 页面,而不是 facebook.com。
It means the user gets the Google page instead of facebook.com on their browser.
在本练习中,我们了解了如何通过不同的工具和方法来嗅探网络流量。这里一家公司需要一位道德黑客为其提供网络安全,以阻止所有这些攻击。让我们了解一下一位道德黑客可以做些什么来防止 DNS 中毒。
In this exercise, we saw how network traffic can be sniffed through different tools and methods. Here a company needs an ethical hacker to provide network security to stop all these attacks. Let’s see what an ethical hacker can do to prevent DNS Poisoning.
Defenses against DNS Poisoning
作为一名道德黑客,您的工作很大可能将您置于预防而不是笔试的位置。您作为攻击者所知道的事情可以帮助您防止从外部采用的技术。
As an ethical hacker, your work could very likely put you in a position of prevention rather than pen testing. What you know as an attacker can help you prevent the very techniques you employ from the outside.
以下是笔试人员的角度对我们刚刚涵盖的攻击进行的防御措施:
Here are defenses against the attacks we just covered from a pen tester’s perspective −
-
Use a hardware-switched network for the most sensitive portions of your network in an effort to isolate traffic to a single segment or collision domain.
-
Implement IP DHCP Snooping on switches to prevent ARP poisoning and spoofing attacks.
-
Implement policies to prevent promiscuous mode on network adapters.
-
Be careful when deploying wireless access points, knowing that all traffic on the wireless network is subject to sniffing.
-
Encrypt your sensitive traffic using an encrypting protocol such as SSH or IPsec.
-
Port security is used by switches that have the ability to be programmed to allow only specific MAC addresses to send and receive data on each port.
-
IPv6 has security benefits and options that IPv4 does not have.
-
Replacing protocols such as FTP and Telnet with SSH is an effective defense against sniffing. If SSH is not a viable solution, consider protecting older legacy protocols with IPsec.
-
Virtual Private Networks (VPNs) can provide an effective defense against sniffing due to their encryption aspect.
-
SSL is a great defense along with IPsec.
Summary
在本章中,我们讨论了攻击者如何通过在网络中放置数据包嗅探器来捕获和分析所有流量。通过一个实时示例,我们了解了从给定网络中获取受害者凭证是多么容易。攻击者使用 MAC 攻击、ARP 和 DNS 中毒攻击来嗅探网络流量并获取电子邮件对话和密码等敏感信息。
In this chapter, we discussed how attackers can capture and analyze all the traffic by placing a packet sniffer in a network. With a real-time example, we saw how easy it is to get the credentials of a victim from a given network. Attackers use MAC attacks, ARP and DNS poisoning attacks to sniff the network traffic and get hold of sensitive information such as email conversations and passwords.
Ethical Hacking - Exploitation
Exploit 是一种程序化软件或脚本,它可以让黑客通过利用漏洞来控制某个系统。黑客一般使用漏洞扫描程序(例如 Nessus、Nexpose、OpenVAS 等)来查找这些漏洞。
Exploitation is a piece of programmed software or script which can allow hackers to take control over a system, exploiting its vulnerabilities. Hackers normally use vulnerability scanners like Nessus, Nexpose, OpenVAS, etc. to find these vulnerabilities.
Metasploit 是一个强有力的工具,可以找到系统中的漏洞。
Metasploit is a powerful tool to locate vulnerabilities in a system.

根据这些漏洞,我们来查找利用。我们将在此讨论一些可以用来查找漏洞的最好的搜索引擎。
Based on the vulnerabilities, we find exploits. Here, we will discuss some of the best vulnerability search engines that you can use.
Exploit Database
是查找与某个漏洞相关的所有利用的位置。
www.exploit-db.com is the place where you can find all the exploits related to a vulnerability.

Common Vulnerabilities and Exposures
常见漏洞和曝光 (CVE) 是信息安全漏洞名称的标准。CVE 是一本公开已知的漏洞和暴露的词典。它可以免费供公众使用。
Common Vulnerabilities and Exposures (CVE) is the standard for information security vulnerability names. CVE is a dictionary of publicly known information security vulnerabilities and exposures. It’s free for public use. https://cve.mitre.org

National Vulnerability Database
国家漏洞数据库 (NVD) 是美国政府基于标准的漏洞管理数据的存储库。这些数据可以实现漏洞管理、安全度量和合规的自动化。您可以在以下位置找到此数据库 −
National Vulnerability Database (NVD) is the U.S. government repository of standards based vulnerability management data. This data enables automation of vulnerability management, security measurement, and compliance. You can locate this database at − https://nvd.nist.gov
NVD 包含安全核对表、与安全相关的软件缺陷、错误配置、产品名称和影响指标的数据库。
NVD includes databases of security checklists, security-related software flaws, misconfigurations, product names, and impact metrics.

总体来说,存在两种类型的利用:
In general, you will see that there are two types of exploits −
-
Remote Exploits − These are the type of exploits where you don’t have access to a remote system or network. Hackers use remote exploits to gain access to systems that are located at remote places.
-
Local Exploits − Local exploits are generally used by a system user having access to a local system, but who wants to overpass his rights.
Quick Fix
漏洞通常由缺少更新而引起,因此建议您定期更新系统(例如,每周一次)。
Vulnerabilities generally arise due to missing updates, so it is recommended that you update your system on a regular basis, for example, once a week.
在 Windows 环境中,您可以通过使用“控制面板”→“系统和安全”→“Windows 更新”中提供的选项来激活自动更新。
In Windows environment, you can activate automatic updates by using the options available in the Control Panel → System and Security → Windows Updates.

在 Linux Centos 中,可以使用以下命令安装自动更新软件包。
In Linux Centos, you can use the following command to install automatic update package.
yum -y install yum-cronEthical Hacking - Enumeration
枚举属于道德黑客的第一阶段,即“信息收集”。这是一项攻击者与受害者建立主动连接并尝试发现尽可能多的攻击向量的过程,可用于进一步利用这些系统。
Enumeration belongs to the first phase of Ethical Hacking, i.e., “Information Gathering”. This is a process where the attacker establishes an active connection with the victim and try to discover as much attack vectors as possible, which can be used to exploit the systems further.
枚举可用于获取信息,例如 −
Enumeration can be used to gain information on −
-
Network shares
-
SNMP data, if they are not secured properly
-
IP tables
-
Usernames of different systems
-
Passwords policies lists
枚举取决于系统提供的服务。它们可以是 −
Enumerations depend on the services that the systems offer. They can be −
-
DNS enumeration
-
NTP enumeration
-
SNMP enumeration
-
Linux/Windows enumeration
-
SMB enumeration
让我们现在讨论一些广泛用于枚举的工具。
Let us now discuss some of the tools that are widely used for Enumeration.
NTP Suite
NTP 套件用于 NTP 枚举。这很重要,因为在网络环境中,您可以找到其他主服务器,帮助主机更新它们的时间,并且您可以在不验证系统的情况下完成此操作。
NTP Suite is used for NTP enumeration. This is important because in a network environment, you can find other primary servers that help the hosts to update their times and you can do it without authenticating the system.
请看以下示例。
Take a look at the following example.
ntpdate 192.168.1.100 01 Sept 12:50:49 ntpdate[627]:
adjust time server 192.168.1.100 offset 0.005030 sec
or
ntpdc [-ilnps] [-c command] [hostname/IP_address]
root@test]# ntpdc -c sysinfo 192.168.1.100
***Warning changing to older implementation
***Warning changing the request packet size from 160 to 48
system peer: 192.168.1.101
system peer mode: client
leap indicator: 00
stratum: 5
precision: -15
root distance: 0.00107 s
root dispersion: 0.02306 s
reference ID: [192.168.1.101]
reference time: f66s4f45.f633e130, Sept 01 2016 22:06:23.458
system flags: monitor ntp stats calibrate
jitter: 0.000000 s
stability: 4.256 ppm
broadcastdelay: 0.003875 s
authdelay: 0.000107 senum4linux
enum4linux 用于枚举 Linux 系统。查看以下屏幕截图并观察我们如何在目标主机中发现用户名。
enum4linux is used to enumerate Linux systems. Take a look at the following screenshot and observe how we have found the usernames present in a target host.

Ethical Hacking - Metasploit
Metasploit 是最强大的攻击工具之一。它的大部分资源可以在以下位置找到: https://www.metasploit.com 。它有两种版本 - commercial 和 free edition 。这两个版本没有大的区别,所以本教程中,我们将主要使用 Metasploit 社区版(免费版)。
Metasploit is one of the most powerful exploit tools. Most of its resources can be found at: https://www.metasploit.com. It comes in two versions − commercial and free edition. There are no major differences in the two versions, so in this tutorial, we will be mostly using the Community version (free) of Metasploit.
作为一名道德黑客,你将使用“Kali Distribution”,其中嵌入了 Metasploit 社区版本以及其他道德黑客工具。但是,如果您想将 Metasploit 作为单独的工具进行安装,则可以在运行 Linux、Windows 或 Mac OS X 的系统上轻松进行。
As an Ethical Hacker, you will be using “Kali Distribution” which has the Metasploit community version embedded in it along with other ethical hacking tools. But if you want to install Metasploit as a separate tool, you can easily do so on systems that run on Linux, Windows, or Mac OS X.
安装 Metasploit 的硬件要求为 −
The hardware requirements to install Metasploit are −
-
2 GHz+ processor
-
1 GB RAM available
-
1 GB+ available disk space
Matasploit can be used either with command prompt or with Web UI.
To open in Kali, go to Applications → Exploitation Tools → metasploit.

After Metasploit starts, you will see the following screen. Highlighted in red underline is the version of Metasploit.

Exploits of Metasploit
通过漏洞扫描程序,我们发现用于测试的 Linux 机器容易受到 FTP 服务攻击。现在,我们要使用可以为我们工作的漏洞利用。命令为:
From Vulnerability Scanner, we found that the Linux machine that we have for test is vulnerable to FTP service. Now, we will use the exploit that can work for us. The command is −
use “exploit path”屏幕将会显示以下内容:
The screen will appear as follows −

然后键入 mfs> show options 以便查看要设置什么参数以使其可用。如图所示,我们必须将 RHOST 设置为“目标 IP”。
Then type mfs> show options in order to see what parameters you have to set in order to make it functional. As shown in the following screenshot, we have to set RHOST as the “target IP”.

We type msf> set RHOST 192.168.1.101 and msf>set RPORT 21

Then, type mfs>run. If the exploit is successful, then it will open one session that you can interact with, as shown in the following screenshot.

Metasploit Payloads
Payload, in simple terms, are simple scripts that the hackers utilize to interact with a hacked system. Using payloads, they can transfer data to a victim system.
Metasploit 负载可以划分为三类 −
Metasploit payloads can be of three types −
-
Singles − Singles are very small and designed to create some kind of communication, then move to the next stage. For example, just creating a user.
-
Staged − It is a payload that an attacker can use to upload a bigger file onto a victim system.
-
Stages − Stages are payload components that are downloaded by Stagers modules. The various payload stages provide advanced features with no size limits such as Meterpreter and VNC Injection.
Payload Usage − Example
We use the command show payloads. With this exploit, we can see the payloads that we can use, and it will also show the payloads that will help us upload /execute files onto a victim system.


To set the payload that we want, we will use the following command −
set PAYLOAD payload/pathSet the listen host and listen port (LHOST, LPORT) which are the attacker IP and port. Then set remote host and port (RPORT, LHOST) which are the victim IP and port.

Type “exploit”. It will create a session as shown below −

Now we can play with the system according to the settings that this payload offers.
Ethical Hacking - Trojan Attacks
特洛伊木马是非复制程序;它们不会通过附着到其他可执行代码来复制自己的代码。它们在未经计算机用户许可或不知情的情况下运行。
Trojans are non-replication programs; they don’t reproduce their own codes by attaching themselves to other executable codes. They operate without the permissions or knowledge of the computer users.
特洛伊木马隐藏在正常进程中。然而,我们应该强调,特洛伊木马只在计算机用户的帮助下感染外部机器,例如点击来自陌生人的电子邮件附件文件、不扫描就插入 USB、打开不安全的 URL。
Trojans hide themselves in healthy processes. However we should underline that Trojans infect outside machines only with the assistance of a computer user, like clicking a file that comes attached with email from an unknown person, plugging USB without scanning, opening unsafe URLs.
木马有几种恶意功能 −
Trojans have several malicious functions −
-
They create backdoors to a system. Hackers can use these backdoors to access a victim system and its files. A hacker can use Trojans to edit and delete the files present on a victim system, or to observe the activities of the victim.
-
Trojans can steal all your financial data like bank accounts, transaction details, PayPal related information, etc. These are called Trojan-Banker.
-
Trojans can use the victim computer to attack other systems using Denial of Services.
-
Trojans can encrypt all your files and the hacker may thereafter demand money to decrypt them. These are Ransomware Trojans.
-
They can use your phones to send SMS to third parties. These are called SMS Trojans.
Trojan Information
如果您发现了病毒并希望进一步调查其功能,那么我们建议您查看以下通常由防病毒供应商提供的病毒数据库。
If you have found a virus and want to investigate further regarding its function, then we will recommend that you have a look at the following virus databases, which are offered generally by antivirus vendors.
-
Kaspersky Virus database − https://www.kaspersky.com
-
F-secure − https://www.f-secure.com
-
Symantec – Virus Encyclopedia − https://www.symantec.com
Ethical Hacking - TCP/IP Hijacking
TCP/IP Hijacking is when an authorized user gains access to a genuine network connection of another user. It is done in order to bypass the password authentication which is normally the start of a session.
In theory, a TCP/IP connection is established as shown below −

要挟持这个连接,有两个可能性−
To hijack this connection, there are two possibilities −
-
Find the seq which is a number that increases by 1, but there is no chance to predict it.
-
The second possibility is to use the Man-in-the-Middle attack which, in simple words, is a type of network sniffing. For sniffing, we use tools like Wireshark or Ethercap.
Example
攻击者监视网络上的数据传输,发现参与连接的两个设备的 IP。
An attacker monitors the data transmission over a network and discovers the IP’s of two devices that participate in a connection.
当黑客发现其中一个用户的 IP 时,他可以通过 DoS 攻击中断另一个用户的连接,然后通过欺骗已断开连接的用户的 IP 来恢复通信。
When the hacker discovers the IP of one of the users, he can put down the connection of the other user by DoS attack and then resume communication by spoofing the IP of the disconnected user.
Shijack
在实践中,最佳的 TCP/IP 劫持工具之一是 Shijack。它是使用 Python 语言开发的,你可以从下面的链接下载它 - https://packetstormsecurity.com/sniffers/shijack.tgz
In practice, one of the best TCP/IP hijack tools is Shijack. It is developed using Python language and you can download it from the following link − https://packetstormsecurity.com/sniffers/shijack.tgz
以下是 Shijack 命令的一个示例 -
Here is an example of a Shijack command −
root:/home/root/hijack# ./shijack eth0 192.168.0.100 53517 192.168.0.200 23
在这里,我们试图劫持两个主机之间的 Telnet 连接。
Here, we are trying to hijack a Telnet connection between the two hosts.
Hunt
Hunt 是另一个你可以用来劫持 TCP/IP 连接的流行工具。它可以从 - https://packetstormsecurity.com/sniffers/hunt/ 下载
Hunt is another popular tool that you can use to hijack a TCP/IP connection. It can be downloaded from − https://packetstormsecurity.com/sniffers/hunt/

Ethical Hacking - Email Hijacking
Email Hijacking, or email hacking, is a widespread menace nowadays. It works by using the following three techniques which are email spoofing, social engineering tools, or inserting viruses in a user computer.
Email Spoofing
In email spoofing, the spammer sends emails from a known domain, so the receiver thinks that he knows this person and opens the mail. Such mails normally contain suspicious links, doubtful content, requests to transfer money, etc.

Social Engineering
Spammers send promotional mails to different users, offering huge discount and tricking them to fill their personal data. You have tools available in Kali that can drive you to hijack an email.

Email hacking can also be done by phishing techniques. See the following screenshot.

The links in the email may install malware on the user’s system or redirect the user to a malicious website and trick them into divulging personal and financial information, such as passwords, account IDs or credit card details.
网络罪犯广泛地使用 Phishing attacks ,因为欺骗某人单击电子邮件中的恶意链接比试图突破计算机防御系统要容易得多。
Phishing attacks are widely used by cybercriminals, as it is far easier to trick someone into clicking a malicious links in the email than trying to break through a computer’s defenses.
Inserting Viruses in a User System
黑客可以劫持电子邮件帐户的第三种技术是通过使用病毒或任何其他类型的恶意软件感染系统。在病毒的帮助下,黑客可以窃取你的所有密码。
The third technique by which a hacker can hijack your email account is by infecting your system with a virus or any other kind of malware. With the help of a virus, a hacker can take all your passwords.
How to detect if your email has been hijacked?
-
The recipients of spam emails include a bunch of people you know.
-
You try to access your account and the password no longer works.
-
You try to access the “Forgot Password” link and it does not go to the expected email.
-
Your Sent Items folder contains a bunch of spams you are not aware of sending.
Quick tips
如果你认为你的电子邮件被劫持了,那么你需要采取以下措施 −
In case you think that your email got hijacked, then you need to take the following actions −
-
Change the passwords immediately.
-
Notify your friends not to open links that they receive from your email account.
-
Contact the authorities and report that your account has been hacked.
-
Install a good antivirus on your computer and update it.
-
Set up double authentication password if it is supported.
Ethical Hacking - Password Hacking
我们有用于电子邮件、数据库、计算机系统、服务器、银行账户和我们想要保护的几乎所有内容的密码。密码通常是进入系统或帐户的密钥。
We have passwords for emails, databases, computer systems, servers, bank accounts, and virtually everything that we want to protect. Passwords are in general the keys to get access into a system or an account.
通常情况下,人们倾向于设置易于记住的密码,例如他们的出生日期、家人的名字、手机号码等。这正是导致密码薄弱且容易被黑客攻击的原因。
In general, people tend to set passwords that are easy to remember, such as their date of birth, names of family members, mobile numbers, etc. This is what makes the passwords weak and prone to easy hacking.
人们应该始终注意使用强密码来保护他们的帐户免受潜在黑客的攻击。强密码具有以下属性:−
One should always take care to have a strong password to defend their accounts from potential hackers. A strong password has the following attributes −
-
Contains at least 8 characters.
-
A mix of letters, numbers, and special characters.
-
A combination of small and capital letters.
Dictionary Attack
在字典攻击中,黑客使用词典中预定义的单词列表来尝试猜测密码。如果设置的密码较弱,则字典攻击可以非常快速地对其进行解码。
In a dictionary attack, the hacker uses a predefined list of words from a dictionary to try and guess the password. If the set password is weak, then a dictionary attack can decode it quite fast.
Hydra 是一个流行的工具,被广泛用于字典攻击。请看以下屏幕截图,了解我们如何使用 Hydra 来找出 FTP 服务的密码。
Hydra is a popular tool that is widely used for dictionary attacks. Take a look at the following screenshot and observe how we have used Hydra to find out the password of an FTP service.

Hybrid Dictionary Attack
混合字典攻击使用字典单词集与扩展名组合。例如,我们有单词“admin”,并将其与数字扩展名(例如“admin123”、“admin147”等)组合在一起。
Hybrid dictionary attack uses a set of dictionary words combined with extensions. For example, we have the word “admin” and combine it with number extensions such as “admin123”, “admin147”, etc.
Crunch 是一个单词列表生成器,您可以在其中指定标准字符集或字符集。 Crunch 可以生成所有可能的组合和排列。此工具与 Linux 的 Kali 发行版捆绑在一起。
Crunch is a wordlist generator where you can specify a standard character set or a character set. Crunch can generate all possible combinations and permutations. This tool comes bundled with the Kali distribution of Linux.

Brute-Force Attack
在暴力攻击中,黑客使用字母、数字、特殊字符、小写字母和大写字母的所有可能组合来破解密码。这种类型的攻击成功的可能性很高,但需要大量的时间来处理所有组合。暴力攻击速度很慢,黑客可能需要一个具有高处理能力的系统来更快地执行所有这些排列和组合。
In a brute-force attack, the hacker uses all possible combinations of letters, numbers, special characters, and small and capital letters to break the password. This type of attack has a high probability of success, but it requires an enormous amount of time to process all the combinations. A brute-force attack is slow and the hacker might require a system with high processing power to perform all those permutations and combinations faster.
John the Ripper 或 Johnny 是设置暴力攻击的强大工具之一,它与 Linux 的 Kali 发行版捆绑在一起。
John the Ripper or Johnny is one of the powerful tools to set a brute-force attack and it comes bundled with the Kali distribution of Linux.

Rainbow Tables
彩虹表包含一组预定义且已散列的密码。它是一个查找表,尤其用于从密码文本中恢复明文密码。在密码恢复过程中,它只需查看预先计算的散列表即可破解密码。这些表可从 http://project-rainbowcrack.com/table.htm 下载
A rainbow table contains a set of predefined passwords that are hashed. It is a lookup table used especially in recovering plain passwords from a cipher text. During the process of password recovery, it just looks at the pre-calculated hash table to crack the password. The tables can be downloaded from http://project-rainbowcrack.com/table.htm
RainbowCrack 1.6.1 是使用彩虹表的工具。它可在 Kali 发行版中再次使用。
RainbowCrack 1.6.1 is the tool to use the rainbow tables. It is available again in Kali distribution.

Ethical Hacking - Wireless Hacking
无线网络是一组两个或多个通过无线电波连接的设备,在有限的空间范围内彼此连接。无线网络中的设备可以自由移动,但可以连接网络并在网络中与其他设备共享数据。它们如此普遍的一个最关键点是,其安装成本非常低,并且比有线网络快。
A wireless network is a set of two or more devices connected with each other via radio waves within a limited space range. The devices in a wireless network have the freedom to be in motion, but be in connection with the network and share data with other devices in the network. One of the most crucial point that they are so spread is that their installation cost is very cheap and fast than the wire networks.
无线网络得到了广泛使用,并且很容易设置。它们使用 IEEE 802.11 标准。 wireless router 是将用户连接到互联网的无线网络中最重要的设备。
Wireless networks are widely used and it is quite easy to set them up. They use IEEE 802.11 standards. A wireless router is the most important device in a wireless network that connects the users with the Internet.

在无线网络中,我们有 Access Points ,它们是作为逻辑交换机工作的无线范围扩展。
In a wireless network, we have Access Points which are extensions of wireless ranges that behave as logical switches.

尽管无线网络提供了极大的灵活性,但它们有其安全问题。黑客无需出现在网络所在的大楼里即可嗅探网络数据包。由于无线网络通过无线电波通信,黑客可以轻松地从附近位置嗅探网络。
Although wireless networks offer great flexibility, they have their security problems. A hacker can sniff the network packets without having to be in the same building where the network is located. As wireless networks communicate through radio waves, a hacker can easily sniff the network from a nearby location.
大多数攻击者使用网络嗅探来查找 SSID 并黑客入侵无线网络。当我们的无线卡转换为嗅探模式时,它们被称为 monitor mode 。
Most attackers use network sniffing to find the SSID and hack a wireless network. When our wireless cards are converted in sniffing modes, they are called monitor mode.
Kismet
Kismet is a powerful tool for wireless sniffing that is found in Kali distribution. It can also be downloaded from its official webpage − https://www.kismetwireless.net
让我们看看它是如何工作的。首先,打开一个终端并键入 kismet 。启动 Kismet 服务器,然后单击“是”,如下面的屏幕截图所示。
Let’s see how it works. First of all, open a terminal and type kismet. Start the Kismet Server and click Yes, as shown in the following screenshot.

如这里所示,单击“开始”按钮。
As shown here, click the Start button.
现在,Kismet 将开始捕获数据。以下屏幕截图显示了它将如何显示 −
Now, Kismet will start to capture data. The following screenshot shows how it would appear −

NetStumbler
NetStumbler 是另一种无线黑客工具,主要用于 Windows 系统。它可以从 http://www.stumbler.net/ 下载
NetStumbler is another tool for wireless hacking that is primarily meant for Windows systems. It can be downloaded from http://www.stumbler.net/
在系统上使用 NetStumbler 非常容易。你只需单击“扫描”按钮并等待结果,如下面的屏幕截图所示。
It is quite easy to use NetStumbler on your system. You just have to click the Scanning button and wait for the result, as shown in the following screenshot.

它应显示如下屏幕截图 −
It should display a screenshot as follows −

需要注意的是你的卡应支持监视模式,否则你将无法监视。
It is important to note that your card should support monitoring mode, otherwise you will fail to monitor.
Wired Equivalent Privacy
有线等效保密(WEP)是一种安全协议,旨在保护无线网络并保持其私密性。它利用数据链路层的加密来禁止对网络的未经授权访问。
Wired Equivalent Privacy (WEP) is a security protocol that was invented to secure wireless networks and keep them private. It utilizes encryption at the data link layer which forbids unauthorized access to the network.
在传输开始之前,使用该密钥加密分组。完整性检查机制 检查分组在传输后未被更改。
The key is used to encrypt the packets before transmission begins. An *integrity check mechanism *checks that the packets are not altered after transmission.
请注意,WEP 并非完全不受安全问题影响。它会遇到以下几个问题:
Note that WEP is not entirely immune to security problems. It suffers from the following issues −
-
CRC32 is not sufficient to ensure complete cryptographic integrity of a packet.
-
It is vulnerable to dictionary attacks.
-
WEP is vulnerable to Denial of Services attacks too.
WEPcrack
WEPcrack 是一种流行的破解 WEP 密码工具。它可以从以下位置下载: https://sourceforge.net/projects/wepcrack/
WEPcrack is a popular tool to crack WEP passwords. It can be downloaded from − https://sourceforge.net/projects/wepcrack/

Aircrack-ng
Aircrak-ng 是另一种破解 WEP 密码的流行工具。它可以在 Linux 的 Kali 发行版中找到。
Aircrak-ng is another popular tool for cracking WEP passwords. It can be found in the Kali distribution of Linux.
以下屏幕截图显示了我们如何嗅探无线网络以及收集分组,并创建了文件 RHAWEP-01.cap。然后我们使用 aircrack-ng 运行该文件,以解密密码。
The following screenshot shows how we have sniffed a wireless network and collected packets and created a file RHAWEP-01.cap. Then we run it with aircrack-ng to decrypt the cypher.

Wireless DoS Attacks
在无线环境中,攻击者可以远距离攻击网络,因此有时难以收集针对攻击者的证据。
In a wireless environment, an attacker can attack a network from a distance and therefore, it is sometimes difficult to collect evidences against the attacker.
DoS 的第一种类型是 Physical Attack 。这种类型的攻击非常基础,其基础是无线电干扰,这种干扰甚至可以用 2.4 GHz 范围内运行的无绳电话来创造。
The first type of DoS is Physical Attack. This type of attack is very basic and it is in the base of radio interferences which can be created even from cordless phones that operate in 2.4 GHz range.
另一种类型是 Network DoS Attack 。由于无线接入点创造了一种共享介质,因此它提供了使此介质洪水般涌向接入点(AP)的可能性,从而会降低其对尝试连接的各个客户端的处理速度。此类攻击仅由 ping flood DoS attack 即可创建。
Another type is Network DoS Attack. As the Wireless Access Point creates a shared medium, it offers the possibility to flood the traffic of this medium toward the AP which will make its processing more slow toward the clients that attempt to connect. Such attacks can be created just by a ping flood DoS attack.
Pyloris 是一种流行的 DoS 工具,您可以从以下位置下载: https://sourceforge.net/projects/pyloris/
Pyloris is a popular DoS tool that you can download from − https://sourceforge.net/projects/pyloris/
低轨道离子加农炮 (LOIC) 是一种其他流行的 DoS 攻击工具。
Low Orbit Ion Cannon (LOIC) is another popular tool for DoS attacks.

Quick Tips
要保护无线网络安全,您应该牢记以下几点:
To secure a wireless network, you should keep the following points in mind −
-
Change the SSID and the network password regularly.
-
Change the default password of access points.
-
Don’t use WEP encryption.
-
Turn off guest networking.
-
Update the firmware of your wireless device.
Ethical Hacking - Social Engineering
让我们通过一些示例来了解社会工程攻击的概念。
Let us try to understand the concept of Social Engineering attacks through some examples.
Example 1
你一定注意到过公司将旧文件当作垃圾丢弃在垃圾桶中。这些文件可能包含一些敏感信息,例如姓名、电话号码、帐号、社保号码、地址等。许多公司的传真机仍使用复写纸,一旦卷纸用完,其复写纸就会被丢弃在垃圾桶中,可能会包含敏感数据的痕迹。虽然听起来不太可能,但攻击者可以轻易地从公司的垃圾箱中获取信息,方法是翻找垃圾。
You must have noticed old company documents being thrown into dustbins as garbage. These documents might contain sensitive information such as Names, Phone Numbers, Account Numbers, Social Security Numbers, Addresses, etc. Many companies still use carbon paper in their fax machines and once the roll is over, its carbon goes into dustbin which may have traces of sensitive data. Although it sounds improbable, but attackers can easily retrieve information from the company dumpsters by pilfering through the garbage.
Example 2
一个攻击者可能会和一个公司职员交朋友,并在一段时间内与其建立良好的关系。这种关系可以通过社交网络、聊天室在线建立,也可以在咖啡馆、操场上或通过任何其他方式进行线下建立。攻击者会取得公司职员的信任,并最终在不留任何线索的情况下获取所需的敏感信息。
An attacker may befriend a company personnel and establish good relationship with him over a period of time. This relationship can be established online through social networks, chatting rooms, or offline at a coffee table, in a playground, or through any other means. The attacker takes the office personnel in confidence and finally digs out the required sensitive information without giving a clue.
Example 3
一个社会工程师可能会通过伪造身份识别卡或者通过说服员工相信他在公司的职位来冒充一个员工或合法用户或 VIP。这样的攻击者可以获得对受限区域的物理访问权限,从而为攻击提供更多机会。
A social engineer may pretend to be an employee or a valid user or an VIP by faking an identification card or simply by convincing employees of his position in the company. Such an attacker can gain physical access to restricted areas, thus providing further opportunities for attacks.
Example 4
在大多数情况下,攻击者可能会在你周围,而且在你输入用户 ID 和密码、帐户 PIN 等敏感信息时会执行 shoulder surfing 。
It happens in most of the cases that an attacker might be around you and can do shoulder surfing while you are typing sensitive information like user ID and password, account PIN, etc.
Phishing Attack
网络钓鱼攻击是一种基于计算机的社会工程,攻击者会制作一封看起来合法的电子邮件。此类电子邮件看起来和感觉与从原始网站接收的电子邮件一样,但它们可能包含指向虚假网站的链接。如果你不够聪明,那么你就会输入你的用户 ID 和密码并尝试登录,这样将会导致失败,而那时,攻击者已经得到了你的 ID 和密码来攻击你的原始帐户。
A phishing attack is a computer-based social engineering, where an attacker crafts an email that appears legitimate. Such emails have the same look and feel as those received from the original site, but they might contain links to fake websites. If you are not smart enough, then you will type your user ID and password and will try to login which will result in failure and by that time, the attacker will have your ID and password to attack your original account.
Quick Fix
-
You should enforce a good security policy in your organization and conduct required trainings to make all the employees aware of the possible Social Engineering attacks and their consequences.
-
Document shredding should be a mandatory activity in your company.
-
Make double sure that any links that you receive in your email is coming from authentic sources and that they point to correct websites. Otherwise you might end up as a victim of Phishing.
-
Be professional and never share your ID and password with anybody else in any case.
Ethical Hacking - DDOS Attacks
分布式拒绝服务 (DDoS) 攻击是一种通过从多个源生成大量流量来使在线服务或网站不可用的尝试。
A Distributed Denial of Service (DDoS) attack is an attempt to make an online service or a website unavailable by overloading it with huge floods of traffic generated from multiple sources.
与拒绝服务 (DoS) 攻击不同,在拒绝服务 (DoS) 攻击中,使用一台计算机和一个 Internet 连接向目标资源发送大量数据包,分布式拒绝服务 (DDoS) 攻击使用多台计算机和多个 Internet 连接,通常在全球范围内分布,称为 botnet 。
Unlike a Denial of Service (DoS) attack, in which one computer and one Internet connection is used to flood a targeted resource with packets, a DDoS attack uses many computers and many Internet connections, often distributed globally in what is referred to as a botnet.
大规模体积 DDoS 攻击可以产生每秒以十千兆比特(甚至数百千兆比特)衡量的流量。我们确信您的普通网络将无法处理此类流量。
A large scale volumetric DDoS attack can generate a traffic measured in tens of Gigabits (and even hundreds of Gigabits) per second. We are sure your normal network will not be able to handle such traffic.
What are Botnets?
攻击者构建一个黑客机器网络,这些机器被称为 botnets ,通过电子邮件、网站和社交媒体传播恶意代码段。一旦这些计算机受到感染,就可以在没有其所有者知情的情况下进行远程控制,并像一支军队一样用来对任何目标发动攻击。
Attackers build a network of hacked machines which are known as botnets, by spreading malicious piece of code through emails, websites, and social media. Once these computers are infected, they can be controlled remotely, without their owners' knowledge, and used like an army to launch an attack against any target.

DDoS 洪流可以通过多种方式生成。例如 −
A DDoS flood can be generated in multiple ways. For example −
-
Botnets can be used for sending more number of connection requests than a server can handle at a time.
-
Attackers can have computers send a victim resource huge amounts of random data to use up the target’s bandwidth.
由于这些机器的分布式特性,它们可用于生成难以处理的分布式高流量。最后导致服务完全阻塞。
Due to the distributed nature of these machines, they can be used to generate distributed high traffic which may be difficult to handle. It finally results in a complete blockage of a service.
Types of DDoS Attacks
DDoS 攻击可以大致分为三种类型−
DDoS attacks can be broadly categorized into three categories −
-
Volume-based Attacks
-
Protocol Attacks
-
Application Layer Attacks
Volume-Based Attacks
基于容量的攻击包括 TCP 泛洪、UDP 泛洪、ICMP 泛洪和其他欺骗数据包泛洪。这些攻击也称为 Layer 3 & 4 Attacks 。在此,攻击者试图使目标站点的带宽饱和。攻击幅度以 Bits per Second (bps) 为单位来衡量。
Volume-based attacks include TCP floods, UDP floods, ICMP floods, and other spoofedpacket floods. These are also called Layer 3 & 4 Attacks. Here, an attacker tries to saturate the bandwidth of the target site. The attack magnitude is measured in Bits per Second (bps).
-
UDP Flood − A UDP flood is used to flood random ports on a remote host with numerous UDP packets, more specifically port number 53. Specialized firewalls can be used to filter out or block malicious UDP packets.
-
ICMP Flood − This is similar to UDP flood and used to flood a remote host with numerous ICMP Echo Requests. This type of attack can consume both outgoing and incoming bandwidth and a high volume of ping requests will result in overall system slowdown.
-
HTTP Flood − The attacker sends HTTP GET and POST requests to a targeted web server in a large volume which cannot be handled by the server and leads to denial of additional connections from legitimate clients.
-
Amplification Attack − The attacker makes a request that generates a large response which includes DNS requests for large TXT records and HTTP GET requests for large files like images, PDFs, or any other data files.
Protocol Attacks
协议攻击包括 SYN 洪水,死亡之 ping,碎片分组攻击,Smurf DDoS 等。这种类型的攻击会占用实际的服务器资源和其他资源,如防火墙和负载平衡器。攻击级别是用 Packets per Second 来衡量的。
Protocol attacks include SYN floods, Ping of Death, fragmented packet attacks, Smurf DDoS, etc. This type of attack consumes actual server resources and other resources like firewalls and load balancers. The attack magnitude is measured in Packets per Second.
-
DNS Flood − DNS floods are used for attacking both the infrastructure and a DNS application to overwhelm a target system and consume all its available network bandwidth.
-
SYN Flood − The attacker sends TCP connection requests faster than the targeted machine can process them, causing network saturation. Administrators can tweak TCP stacks to mitigate the effect of SYN floods. To reduce the effect of SYN floods, you can reduce the timeout until a stack frees memory allocated to a connection, or selectively dropping incoming connections using a firewall or iptables.
-
Ping of Death − The attacker sends malformed or oversized packets using a simple ping command. IP allows sending 65,535 bytes packets but sending a ping packet larger than 65,535 bytes violates the Internet Protocol and could cause memory overflow on the target system and finally crash the system. To avoid Ping of Death attacks and its variants, many sites block ICMP ping messages altogether at their firewalls.
Application Layer Attacks
应用程序层攻击包括 Slowloris、零日 DDoS 攻击、针对 Apache、Windows 或 OpenBSD 漏洞的 DDoS 攻击等。这里的目标是使 Web 服务器崩溃。攻击强度以 Requests per Second 为单位。
Application Layer Attacks include Slowloris, Zero-day DDoS attacks, DDoS attacks that target Apache, Windows or OpenBSD vulnerabilities and more. Here the goal is to crash the web server. The attack magnitude is measured in Requests per Second.
-
Application Attack − This is also called Layer 7 Attack, where the attacker makes excessive log-in, database-lookup, or search requests to overload the application. It is really difficult to detect Layer 7 attacks because they resemble legitimate website traffic.
-
Slowloris − The attacker sends huge number of HTTP headers to a targeted web server, but never completes a request. The targeted server keeps each of these false connections open and eventually overflows the maximum concurrent connection pool, and leads to denial of additional connections from legitimate clients.
-
NTP Amplification − The attacker exploits publically-accessible Network Time Protocol (NTP) servers to overwhelm the targeted server with User Datagram Protocol (UDP) traffic.
-
Zero-day DDoS Attacks − A zero-day vulnerability is a system or application flaw previously unknown to the vendor, and has not been fixed or patched. These are new type of attacks coming into existence day by day, for example, exploiting vulnerabilities for which no patch has yet been released.
How to Fix a DDoS Attack
您可以应用的 DDoS 保护选项有很多,这取决于 DDoS 攻击的类型。
There are quite a few DDoS protection options which you can apply depending on the type of DDoS attack.
您的 DDoS 保护从识别和关闭系统中所有可能的 OS 和应用程序级别漏洞开始,关闭所有可能的端口,从系统中删除不必要的访问权限,并在代理或 CDN 系统后面隐藏您的服务器。
Your DDoS protection starts from identifying and closing all the possible OS and application level vulnerabilities in your system, closing all the possible ports, removing unnecessary access from the system and hiding your server behind a proxy or CDN system.
如果您发现 DDoS 攻击的强度较低,那么您可以找到许多基于防火墙的解决方案,这些解决方案可以帮助您过滤掉基于 DDoS 的流量。但如果您遭受大流量 DDoS 攻击(如千兆位或更多),那么您应该寻求 DDoS 保护服务提供商的帮助,该服务提供商提供更全面、主动和真实的方法。
If you see a low magnitude of the DDoS, then you can find many firewall-based solutions which can help you in filtering out DDoS based traffic. But if you have high volume of DDoS attack like in gigabits or even more, then you should take the help of a DDoS protection service provider that offers a more holistic, proactive and genuine approach.
在选择和选择 DDoS 保护服务提供商时,您必须小心。有许多服务提供商想要利用您的处境。如果您告诉他们您正在受到 DDoS 攻击,那么他们将开始以不合理的高成本向您提供各种服务。
You must be careful while approaching and selecting a DDoS protection service provider. There are number of service providers who want to take advantage of your situation. If you inform them that you are under DDoS attack, then they will start offering you a variety of services at unreasonably high costs.
我们可以向您建议一个简单有效的解决方案,它从寻找一个出色的 DNS 解决方案提供商开始,该提供商足够灵活,可以为您的网站配置 A 和 CNAME 记录。其次,您将需要一个出色的 CDN 提供商,它可以处理大量的 DDoS 流量,并作为其 CDN 软件包的一部分为您提供 DDoS 保护服务。
We can suggest you a simple and working solution which starts with a search for a good DNS solution provider who is flexible enough to configure A and CNAME records for your website. Second, you will need a good CDN provider that can handle big DDoS traffic and provide you DDoS protection service as a part of their CDN package.
假设您的服务器 IP 地址为 AAA.BBB.CCC.DDD。然后,您应该执行以下 DNS 配置 −
Assume your server IP address is AAA.BBB.CCC.DDD. Then you should do the following DNS configuration −
-
Create a A Record in DNS zone file as shown below with a DNS identifier, for example, ARECORDID and keep it secret from the outside world.
-
Now ask your CDN provider to link the created DNS identifier with a URL, something like cdn.someotherid.domain.com.
-
You will use the CDN URL cdn.someotherid.domain.com to create two CNAME records, the first one to point to www and the second record to point to @ as shown below.
你可以向系统管理员寻求帮助,以便理解这些要点并适当地配置 DNS 和 CDN。最后,你将在 DNS 中获得如下配置。
You can take the help from your system administrator to understand these points and configure your DNS and CDN appropriately. Finally, you will have the following configuration at your DNS.

现在,让 CDN 提供商处理所有类型的 DDoS 攻击,你的系统将保持安全。但前提是你不得向任何人透露系统的 IP 地址或 A 记录标识符,否则直接攻击将重新开始。
Now, let the CDN provider handle all type of DDoS attacks and your system will remain safe. But here the condition is that you should not disclose your system’s IP address or A record identifier to anyone; else direct attacks will start again.
Quick Fix
DDoS 攻击比以往任何时候都更加常见,不幸的是,对于此问题没有快速修复方法。但是,如果你的系统受到 DDoS 攻击,请不要惊慌,开始逐步调查此事。
DDoS attacks have become more common than ever before, and unfortunately, there is no quick fix for this problem. However, if your system is under a DDoS attack, then don’t panic and start looking into the matter step by step.
Ethical Hacking - Cross-Site Scripting
Cross-site scripting (XSS) is a code injection attack that allows an attacker to execute malicious JavaScript in another user’s browser.
The attacker does not directly target his victim. Instead, he exploits a vulnerability in a website that the victim visits, in order to get the website to deliver the malicious JavaScript for him. To the victim’s browser, the malicious JavaScript appears to be a legitimate part of the website, and the website has thus acted as an unintentional accomplice to the attacker. These attacks can be carried out using HTML, JavaScript, VBScript, ActiveX, Flash, but the most used XSS is malicious JavaScript.
These attacks also can gather data from account hijacking, changing of user settings, cookie theft/poisoning, or false advertising and create DoS attacks.
Example
让我们通过一个示例了解它的工作原理。我们有一个 metasploitable 机器获取的一个易受攻击的网页。现在,我们将测试用红色箭头高亮显示的域,以针对 XSS。
Let’s take an example to understand how it works. We have a vulnerable webpage that we got by the metasploitable machine. Now we will test the field that is highlighted in red arrow for XSS.

首先,我们编写一个简单的警报脚本
First of all, we make a simple alert script
<script>
alert(‘I am Vulnerable’)
</script>它将生成如下输出:
It will produce the following output −

Types of XSS Attacks
XSS 攻击通常分为三种类型:
XSS attacks are often divided into three types −
-
Persistent XSS, where the malicious string originates from the website’s database.
-
Reflected XSS, where the malicious string originates from the victim’s request.
-
DOM-based XSS, where the vulnerability is in the client-side code rather than the server-side code.
一般而言,可以通过 vulnerability scanners 找到跨站脚本攻击,这样您不必在其中放置 JavaScript 来进行全部手动工作,例如
Generally, cross-site scripting is found by vulnerability scanners so that you don’t have to do all the manual job by putting a JavaScript on it like
<script>
alert('XSS')
</script>Burp Suite 和 acunetix 被认为是最好的漏洞扫描程序。
Burp Suite and acunetix are considered as the best vulnerability scanners.
Ethical Hacking - SQL Injection
SQL injection is a set of SQL commands that are placed in a URL string or in data structures in order to retrieve a response that we want from the databases that are connected with the web applications. This type of attacks generally takes place on webpages developed using PHP or ASP.NET.
SQL 注入攻击可用于以下目的 −
An SQL injection attack can be done with the following intentions −
-
To dump the whole database of a system,
-
To modify the content of the databases, or
-
To perform different queries that are not allowed by the application.
这种类型的攻击在应用程序在将输入传递到 SQL 语句之前没有正确地验证输入时起作用。注入通常放置在地址栏、搜索字段或数据字段中。
This type of attack works when the applications don’t validate the inputs properly, before passing them to an SQL statement. Injections are normally placed put in address bars, search fields, or data fields.
检测 Web 应用程序是否容易受到 SQL 注入攻击的最简单的方法是在字符串中使用“'”字符,然后查看是否出现任何错误。
The easiest way to detect if a web application is vulnerable to an SQL injection attack is to use the " ‘ " character in a string and see if you get any error.
Example 1
让我们使用几个示例来了解这个概念。如图所示,我们在“Name”字段中使用了一个“'”字符。
Let’s try to understand this concept using a few examples. As shown in the following screenshot, we have used a " ‘ " character in the Name field.

现在,单击“ Login ”按钮。它应该产生以下响应 −
Now, click the Login button. It should produce the following response −

这意味着“Name”字段容易受到 SQL 注入攻击。
It means that the “Name” field is vulnerable to SQL injection.
Example 2
We have this URL − http://10.10.10.101/mutillidae/index.php?page=site-footer-xssdiscussion.php
我们希望测试变量“page”,但请观察我们如何在字符串 URL 中注入了一个“'”字符。
And we want to test the variable “page” but observe how we have injected a " ‘ " character in the string URL.

当我们按 Enter 时,它将产生以下结果,其中包含错误。
When we press Enter, it will produce the following result which is with errors.

SQLMAP
SQLMAP 是用于检测 SQL 注入的最佳工具之一。可从 http://sqlmap.org/ 下载。
SQLMAP is one of the best tools available to detect SQL injections. It can be downloaded from http://sqlmap.org/
此工具在 Kali 发行版中,经过预编译。您可以在-应用程序→数据库评估→SQLmap 中找到此工具。
It comes pre-compiled in the Kali distribution. You can locate it at − Applications → Database Assessment → Sqlmap.
在打开 SQLMAP 后,我们转到有 SQL 注入的页面,然后获取标头请求。从标头中,我们在 SQL 中运行以下命令 -
After opening SQLMAP, we go to the page that we have the SQL injection and then get the header request. From the header, we run the following command in SQL −
./sqlmap.py --headers="User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux i686; rv:25.0)
Gecko/20100101 Firefox/25.0" --cookie="security=low;
PHPSESSID=oikbs8qcic2omf5gnd09kihsm7" -u '
http://localhost/dvwa/vulnerabilities/sqli_blind/?id=1&Submit=Submit#' -
level=5 risk=3 -p id --suffix="-BR" -v3SQLMAP 将测试所有变量,结果将显示参数“id”容易受到攻击,如下面的屏幕截图所示。
The SQLMAP will test all the variables and the result will show that the parameter “id” is vulnerable, as shown in the following screenshot.

SQLNinja
SQLNinja 是 Kali 发行版中提供的一种 SQL 注入工具。
SQLNinja is another SQL injection tool that is available in Kali distribution.

JSQL Injection
JSQL Injection 使用 Java 编写,它进行自动化 SQL 注入。
JSQL Injection is in Java and it makes automated SQL injections.

Quick Tips
要防止 Web 应用程序遭受 SQL 注入攻击,您应该记住以下要点:
To prevent your web application from SQL injection attacks, you should keep the following points in mind −
-
Unchecked user-input to database should not be allowed to pass through the application GUI.
-
Every variable that passes into the application should be sanitized and validated.
-
The user input which is passed into the database should be quoted.
Ethical Hacking - Pen Testing
渗透测试是许多公司用来最大程度减少其安全漏洞的方法。这是一种受控方式,由专业人员试图入侵您的系统并向您展示您应该修复的漏洞。
Penetration Testing is a method that many companies follow in order to minimize their security breaches. This is a controlled way of hiring a professional who will try to hack your system and show you the loopholes that you should fix.
在执行渗透测试之前,必须达成一项协议,该协议将明确提及以下参数 -
Before doing a penetration test, it is mandatory to have an agreement that will explicitly mention the following parameters −
-
what will be the time of penetration test,
-
where will be the IP source of the attack, and
-
what will be the penetration fields of the system.
渗透测试是由专业道德黑客执行的,他们主要使用商业的、开源工具、自动化工具和手动检查。没有限制;此处最重要的目标是尽可能发现更多安全漏洞。
Penetration testing is conducted by professional ethical hackers who mainly use commercial, open-source tools, automate tools and manual checks. There are no restrictions; the most important objective here is to uncover as many security flaws as possible.
Types of Penetration Testing
我们有五种渗透测试 -
We have five types of penetration testing −
-
Black Box − Here, the ethical hacker doesn’t have any information regarding the infrastructure or the network of the organization that he is trying to penetrate. In black-box penetration testing, the hacker tries to find the information by his own means.
-
Grey Box − It is a type of penetration testing where the ethical hacker has a partial knowledge of the infrastructure, like its domain name server.
-
White Box − In white-box penetration testing, the ethical hacker is provided with all the necessary information about the infrastructure and the network of the organization that he needs to penetrate.
-
External Penetration Testing − This type of penetration testing mainly focuses on network infrastructure or servers and their software operating under the infrastructure. In this case, the ethical hacker tries the attack using public networks through the Internet. The hacker attempts to hack the company infrastructure by attacking their webpages, webservers, public DNS servers, etc.
-
Internal Penetration Testing − In this type of penetration testing, the ethical hacker is inside the network of the company and conducts his tests from there.
渗透测试还可能导致问题,例如系统故障、系统崩溃或数据丢失。因此,公司在进行渗透测试之前应权衡利弊。风险计算如下,并且是管理风险。
Penetration testing can also cause problems such as system malfunctioning, system crashing, or data loss. Therefore, a company should take calculated risks before going ahead with penetration testing. The risk is calculated as follows and it is a management risk.
RISK = Threat × Vulnerability
RISK = Threat × Vulnerability
Example
您有一个处于生产中的在线电子商务网站。您想在使其上线之前进行渗透测试。在这里,您必须首先权衡利弊。如果您继续进行渗透测试,可能会导致服务中断。相反,如果您不想执行渗透测试,那么您就有可能面临未修补的漏洞的风险,并且该漏洞将始终构成威胁。
You have an online e-commerce website that is in production. You want to do a penetration testing before making it live. Here, you have to weigh the pros and cons first. If you go ahead with penetration testing, it might cause interruption of service. On the contrary, if you do not wish to perform a penetration testing, then you can run the risk of having an unpatched vulnerability that will remain as a threat all the time.
在进行渗透测试之前,建议您书面记录该项目的范围。您应该明确要测试的内容。例如 -
Before doing a penetration test, it is recommended that you put down the scope of the project in writing. You should be clear about what is going to be tested. For example −
-
Your company has a VPN or any other remote access techniques and you want to test that particular point.
-
Your application has webservers with databases, so you might want to get it tested for SQL injection attacks which is one of the most crucial tests on a webserver. In addition, you can check if your webserver is immune to DoS attacks.
Quick Tips
在进行渗透测试之前,您应该牢记以下要点:
Before going ahead with a penetration test, you should keep the following points in mind −
-
First understand your requirements and evaluate all the risks.
-
Hire a certified person to conduct penetration test because they are trained to apply all the possible methods and techniques to uncover possible loopholes in a network or web application.
-
Always sign an agreement before doing a penetration test.
