Ethical Hacking 简明教程
Ethical Hacking - Sniffing
嗅探是使用嗅探工具监控和捕获通过给定网络的所有数据包的过程。这是一种“窃听电话线”并了解对话的形式。它也被称为 wiretapping 应用于计算机网络。
Sniffing is the process of monitoring and capturing all the packets passing through a given network using sniffing tools. It is a form of “tapping phone wires” and get to know about the conversation. It is also called wiretapping applied to the computer networks.
如果一组企业交换机端口已打开,就有很大的可能性,他们的一名员工可以嗅探网络的全部流量。任何在相同物理位置的人都可以使用以太网电缆连接到网络,或以无线方式连接到该网络并嗅探全部流量。
There is so much possibility that if a set of enterprise switch ports is open, then one of their employees can sniff the whole traffic of the network. Anyone in the same physical location can plug into the network using Ethernet cable or connect wirelessly to that network and sniff the total traffic.
换句话说,嗅探使您可以查看各种流量,包括受保护和不受保护的流量。在条件合适且实施了正确的协议时,攻击方有可能收集可用于进一步攻击或给网络或系统所有者造成其他问题的信息。
In other words, Sniffing allows you to see all sorts of traffic, both protected and unprotected. In the right conditions and with the right protocols in place, an attacking party may be able to gather information that can be used for further attacks or to cause other issues for the network or system owner.
What can be sniffed?
人们可以从网络中嗅探以下敏感信息——
One can sniff the following sensitive information from a network −
-
Email traffic
-
FTP passwords
-
Web traffics
-
Telnet passwords
-
Router configuration
-
Chat sessions
-
DNS traffic
How it works
嗅探器通常将系统的 NIC 转到 promiscuous mode ,以便它监听在其网段上传输的所有数据。
A sniffer normally turns the NIC of the system to the promiscuous mode so that it listens to all the data transmitted on its segment.
混杂模式是指以太网硬件(特别是网络接口卡 (NIC))的独特方式,它允许 NIC 接收网络上的所有流量,即使该流量不是针对此 NIC 的。默认情况下,NIC 会忽略所有未发送给它的流量,这是通过将以太网数据包的目标地址与设备的硬件地址(也称为 MAC)进行比较来完成的。虽然这对于网络来说很有意义,但是非混杂模式使得难以使用网络监视和分析软件来诊断连接问题或流量利用率。
Promiscuous mode refers to the unique way of Ethernet hardware, in particular, network interface cards (NICs), that allows an NIC to receive all traffic on the network, even if it is not addressed to this NIC. By default, a NIC ignores all traffic that is not addressed to it, which is done by comparing the destination address of the Ethernet packet with the hardware address (a.k.a. MAC) of the device. While this makes perfect sense for networking, non-promiscuous mode makes it difficult to use network monitoring and analysis software for diagnosing connectivity issues or traffic accounting.
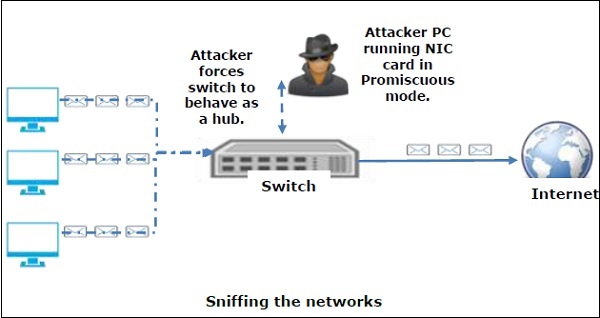
嗅探器可以通过解码数据包中封装的信息,持续监视通过网卡传输到计算机的所有流量。
A sniffer can continuously monitor all the traffic to a computer through the NIC by decoding the information encapsulated in the data packets.
Types of Sniffing
嗅探本质上可分为主动或被动。
Sniffing can be either Active or Passive in nature.
Passive Sniffing
在被动嗅探中,流量被锁定,但不会以任何方式被改变。被动嗅探只允许监听。它适用于集线器设备。在集线器设备上,流量会被发送到所有端口。在一个使用集线器连接系统的网络中,网络上的所有主机都可以看到流量。因此,攻击者可以轻松捕获流量。
In passive sniffing, the traffic is locked but it is not altered in any way. Passive sniffing allows listening only. It works with Hub devices. On a hub device, the traffic is sent to all the ports. In a network that uses hubs to connect systems, all hosts on the network can see the traffic. Therefore, an attacker can easily capture traffic going through.
好消息是,如今集线器几乎已经过时了。大多数现代网络使用交换机。因此,被动嗅探不再有效。
The good news is that hubs are almost obsolete nowadays. Most modern networks use switches. Hence, passive sniffing is no more effective.
Active Sniffing
在主动嗅探中,流量不仅被锁定和监控,而且可能会根据攻击者的决定以某种方式被改变。主动嗅探用于嗅探基于交换机的网络。它涉及向目标网络注入 address resolution packets (ARP),以在交换机 content addressable memory (CAM)表中泛洪。CAM 会跟踪每个主机连接到哪个端口。
In active sniffing, the traffic is not only locked and monitored, but it may also be altered in some way as determined by the attack. Active sniffing is used to sniff a switch-based network. It involves injecting address resolution packets (ARP) into a target network to flood on the switch content addressable memory (CAM) table. CAM keeps track of which host is connected to which port.
以下是主动嗅探技术——
Following are the Active Sniffing Techniques −
-
MAC Flooding
-
DHCP Attacks
-
DNS Poisoning
-
Spoofing Attacks
-
ARP Poisoning
Protocols which are affected
诸如久经考验的 TCP/IP 等协议在设计时从未考虑安全性,因此对潜在攻击者几乎没有抵抗力。几条规则很容易被嗅探 −
Protocols such as the tried and true TCP/IP were never designed with security in mind and therefore do not offer much resistance to potential intruders. Several rules lend themselves to easy sniffing −
-
HTTP − It is used to send information in the clear text without any encryption and thus a real target.
-
SMTP (Simple Mail Transfer Protocol) − SMTP is basically utilized in the transfer of emails. This protocol is efficient, but it does not include any protection against sniffing.
-
NNTP (Network News Transfer Protocol)− It is used for all types of communications, but its main drawback is that data and even passwords are sent over the network as clear text.
-
POP (Post Office Protocol) − POP is strictly used to receive emails from the servers. This protocol does not include protection against sniffing because it can be trapped.
-
FTP (File Transfer Protocol) − FTP is used to send and receive files, but it does not offer any security features. All the data is sent as clear text that can be easily sniffed.
-
IMAP (Internet Message Access Protocol) − IMAP is same as SMTP in its functions, but it is highly vulnerable to sniffing.
-
Telnet − Telnet sends everything (usernames, passwords, keystrokes) over the network as clear text and hence, it can be easily sniffed.
嗅探器并不是只能让你查看实时流量的简单工具。如果你真的想要对每个数据包进行分析,请保存捕获内容并在时间允许时对其进行查看。
Sniffers are not the dumb utilities that allow you to view only live traffic. If you really want to analyze each packet, save the capture and review it whenever time allows.
Hardware Protocol Analyzers
在我们进一步了解嗅探器之前,讨论 hardware protocol analyzers 很重要。这些设备会在硬件级别插入网络,并且可以监视流量而不会对其进行操纵。
Before we go into further details of sniffers, it is important that we discuss about hardware protocol analyzers. These devices plug into the network at the hardware level and can monitor traffic without manipulating it.
-
Hardware protocol analyzers are used to monitor and identify malicious network traffic generated by hacking software installed in the system.
-
They capture a data packet, decode it, and analyze its content according to certain rules.
-
Hardware protocol analyzers allow attackers to see individual data bytes of each packet passing through the cable.
由于在许多情况下成本非常高,因此大多数道德黑客无法轻易获得这些硬件设备。
These hardware devices are not readily available to most ethical hackers due to their enormous cost in many cases.
Lawful Interception
合法截取(LI)被定义为合法获取通信网络数据(如电话呼叫或电子邮件)的途径。LI 始终必须为了分析或证据的目的而追求合法权限。因此,法律截取是一种安全流程,其中网络运营商或服务供应商允许执法人员访问个人或组织的私人通信。
Lawful Interception (LI) is defined as legally sanctioned access to communications network data such as telephone calls or email messages. LI must always be in pursuance of a lawful authority for the purpose of analysis or evidence. Therefore, LI is a security process in which a network operator or service provider gives law enforcement officials permission to access private communications of individuals or organizations.
几乎所有国家都起草并颁布了法规来规范合法截取程序;标准化组织正在制定 LI 技术规范。通常,LI 活动是为了基础设施保护和网络安全的目的而进行。然而,除非另有禁止,私人网络基础设施的运营商可以在其自己的网络内保留 LI 功能,作为固有权利。
Almost all countries have drafted and enacted legislation to regulate lawful interception procedures; standardization groups are creating LI technology specifications. Usually, LI activities are taken for the purpose of infrastructure protection and cyber security. However, operators of private network infrastructures can maintain LI capabilities within their own networks as an inherent right, unless otherwise prohibited.
LI 以前称为 wiretapping ,并且自电子通信出现以来就已存在。
LI was formerly known as wiretapping and has existed since the inception of electronic communications.